Quote for the day:
“Become the kind of leader that people would follow voluntarily, even if you had no title or position.” -- Brian Tracy
DevSecOps 2.0: How Security-First DevOps Is Redefining Software Delivery
 DevSecOps 2.0 is a true security-first revolution. This paradigm shift
transforms software security into a proactive enabler, leveraging AI and
policy-as-code to automate safeguards at scale. Security tools now blend
seamlessly into developer workflows, and continuous compliance ensures real-time
auditing. With ransomware, supply chain attacks, and other attacks on the rise,
there is a need for a different approach to delivering resilient software.
... It marks a transformative approach to software development, where
security is the foundation of the entire lifecycle. This evolution ensures
proactive security that works to identify and neutralize threats early. ...
AI-driven security is central to DevSecOps 2.0, which harnesses the power of
artificial intelligence to transform security from a reactive process into a
proactive defense strategy. By analyzing vast datasets, including security logs,
network traffic, and code commit patterns, AI can detect subtle anomalies and
predict potential threats before they materialize. This predictive capability
enables teams to identify risks early, streamlining threat detection and
facilitating automated remediation. For instance, AI can analyze commit patterns
to predict code sections likely to contain vulnerabilities, allowing for
targeted testing and prevention.
DevSecOps 2.0 is a true security-first revolution. This paradigm shift
transforms software security into a proactive enabler, leveraging AI and
policy-as-code to automate safeguards at scale. Security tools now blend
seamlessly into developer workflows, and continuous compliance ensures real-time
auditing. With ransomware, supply chain attacks, and other attacks on the rise,
there is a need for a different approach to delivering resilient software.
... It marks a transformative approach to software development, where
security is the foundation of the entire lifecycle. This evolution ensures
proactive security that works to identify and neutralize threats early. ...
AI-driven security is central to DevSecOps 2.0, which harnesses the power of
artificial intelligence to transform security from a reactive process into a
proactive defense strategy. By analyzing vast datasets, including security logs,
network traffic, and code commit patterns, AI can detect subtle anomalies and
predict potential threats before they materialize. This predictive capability
enables teams to identify risks early, streamlining threat detection and
facilitating automated remediation. For instance, AI can analyze commit patterns
to predict code sections likely to contain vulnerabilities, allowing for
targeted testing and prevention. What CIOs can do when AI boosts performance but kills motivation
 “One of the clearest signs is copy-paste culture,” Anderson says. “When
employees use AI output as-is, without questioning it or tailoring it to their
audience, that’s a sign of disengagement. They’ve stopped thinking critically.”
To prevent this, CIOs can take a closer look at how teams actually use AI.
Honest feedback from employees can help, but there’s often a gap between what
people say they use AI for and how they actually use it in practice, so trying
to detect patterns of copy-paste usage can help improve workflows. CIOs should
also pay attention to how AI affects roles, identities, and team dynamics. When
experienced employees feel replaced, or when previously valued skills are
bypassed, morale can quietly drop, even if productivity remains high on paper.
“In one case, a senior knowledge expert, someone who used to be the go-to for
tough questions, felt displaced when leadership started using AI to get direct
answers,” Anderson says. “His motivation dropped because he felt his value was
being replaced by a tool.” Over time, this expert started to use AI
strategically, and saw it could reduce the ad-hoc noise and give him space for
more strategic work. “That shift from threatened to empowered is something every
leader needs to watch for and support,” he adds.
“One of the clearest signs is copy-paste culture,” Anderson says. “When
employees use AI output as-is, without questioning it or tailoring it to their
audience, that’s a sign of disengagement. They’ve stopped thinking critically.”
To prevent this, CIOs can take a closer look at how teams actually use AI.
Honest feedback from employees can help, but there’s often a gap between what
people say they use AI for and how they actually use it in practice, so trying
to detect patterns of copy-paste usage can help improve workflows. CIOs should
also pay attention to how AI affects roles, identities, and team dynamics. When
experienced employees feel replaced, or when previously valued skills are
bypassed, morale can quietly drop, even if productivity remains high on paper.
“In one case, a senior knowledge expert, someone who used to be the go-to for
tough questions, felt displaced when leadership started using AI to get direct
answers,” Anderson says. “His motivation dropped because he felt his value was
being replaced by a tool.” Over time, this expert started to use AI
strategically, and saw it could reduce the ad-hoc noise and give him space for
more strategic work. “That shift from threatened to empowered is something every
leader needs to watch for and support,” he adds.
That ‘cheap’ open-source AI model is actually burning through your compute budget
 The inefficiency is particularly pronounced for Large Reasoning Models (LRMs),
which use extended “chains of thought” to solve complex problems. These models,
designed to think through problems step-by-step, can consume thousands of tokens
pondering simple questions that should require minimal computation. For basic
knowledge questions like “What is the capital of Australia?” the study found
that reasoning models spend “hundreds of tokens pondering simple knowledge
questions” that could be answered in a single word. ... The research revealed
stark differences between model providers. OpenAI’s models, particularly its
o4-mini and newly released open-source gpt-oss variants, demonstrated
exceptional token efficiency, especially for mathematical problems. The study
found OpenAI models “stand out for extreme token efficiency in math problems,”
using up to three times fewer tokens than other commercial models. ... The
findings have immediate implications for enterprise AI adoption, where computing
costs can scale rapidly with usage. Companies evaluating AI models often focus
on accuracy benchmarks and per-token pricing, but may overlook the total
computational requirements for real-world tasks.
The inefficiency is particularly pronounced for Large Reasoning Models (LRMs),
which use extended “chains of thought” to solve complex problems. These models,
designed to think through problems step-by-step, can consume thousands of tokens
pondering simple questions that should require minimal computation. For basic
knowledge questions like “What is the capital of Australia?” the study found
that reasoning models spend “hundreds of tokens pondering simple knowledge
questions” that could be answered in a single word. ... The research revealed
stark differences between model providers. OpenAI’s models, particularly its
o4-mini and newly released open-source gpt-oss variants, demonstrated
exceptional token efficiency, especially for mathematical problems. The study
found OpenAI models “stand out for extreme token efficiency in math problems,”
using up to three times fewer tokens than other commercial models. ... The
findings have immediate implications for enterprise AI adoption, where computing
costs can scale rapidly with usage. Companies evaluating AI models often focus
on accuracy benchmarks and per-token pricing, but may overlook the total
computational requirements for real-world tasks. AI Agents and the data governance wild west
Today, anyone from an HR director to a marketing intern can quickly build and deploy an AI agent simply using Copilot Studio. This tool is designed to be accessible and quick, making it easy for anyone to play around with and launch a sophisticated agent in no time at all. But when these agents are created outside of the IT department, most users aren’t thinking about data classification or access controls, and they become part of a growing shadow IT problem. ... The problem is that most users will not be thinking like a developer with governance in mind when creating their own agents. Therefore, policies must be imposed to ensure that key security steps aren’t skipped in the rush to deploy a solution. A new layer of data governance must be considered with steps that include configuring data boundaries, restricting who can access what data according to job role and sensitivity level, and clearly specifying which data resources the agent can pull from. AI agents should be built for purpose, using principles of least privilege. This will help avoid a marketing intern having access to the entire company’s HR file. Just like any other business-critical application, it needs to be adequately tested and ‘red-teamed’. Perform penetration testing to identify what data the agent can surface, to who, and how accurate the data is.Monitoring microservices: Best practices for robust systems
 Collecting extensive amounts of telemetry data is most beneficial if you can
combine, visualize and examine it successfully. A unified observability stack is
paramount. By integrating tools like middleware that work together seamlessly,
you create a holistic view of your microservices ecosystem. These unified tools
ensure that all your telemetry information — logs, traces and metrics — is
correlated and accessible from a single pane of glass, dramatically decreasing
the mean time to detect (MTTD) and mean time to resolve (MTTR) problems. The
energy lies in seeing the whole photograph, no longer just remote points. ...
Collecting information is good, but acting on it is better. Define significant
service level objectives (SLOs) that replicate the predicted performance and
reliability of your offerings. ... Monitoring microservices effectively is
an ongoing journey that requires a commitment to standardization of data, using
the right tools and a proactive mindset. By utilizing standardized observability
practices, adapting a unified observability stack, continuously monitoring key
metrics, placing meaningful SLOs and allowing enhanced root cause analysis, you
may construct a strong and resilient microservices structure that truly serves
your business desires and delights your customers.
Collecting extensive amounts of telemetry data is most beneficial if you can
combine, visualize and examine it successfully. A unified observability stack is
paramount. By integrating tools like middleware that work together seamlessly,
you create a holistic view of your microservices ecosystem. These unified tools
ensure that all your telemetry information — logs, traces and metrics — is
correlated and accessible from a single pane of glass, dramatically decreasing
the mean time to detect (MTTD) and mean time to resolve (MTTR) problems. The
energy lies in seeing the whole photograph, no longer just remote points. ...
Collecting information is good, but acting on it is better. Define significant
service level objectives (SLOs) that replicate the predicted performance and
reliability of your offerings. ... Monitoring microservices effectively is
an ongoing journey that requires a commitment to standardization of data, using
the right tools and a proactive mindset. By utilizing standardized observability
practices, adapting a unified observability stack, continuously monitoring key
metrics, placing meaningful SLOs and allowing enhanced root cause analysis, you
may construct a strong and resilient microservices structure that truly serves
your business desires and delights your customers.
How military leadership prepares veterans for cybersecurity success
After dealing with extremely high-pressure environments, in which making the wrong decision can cost lives, veterans and reservists have little trouble dealing with the kinds of risks found in the world of business, such as threats to revenue, brand value and jobs. What’s more, the time-critical mission mindset so essential within the military is highly relevant within cybersecurity, where attacks and breaches must be dealt with confidently, rapidly and calmly. In the armed forces, people often find themselves in situations so intense that Maslow’s hierarchy of needs is flipped on its head. You’re not aiming for self-actualization or more advanced goals, but simply trying to keep the team alive and maintain essential operations. ... Military experience, on the other hand, fosters unparalleled trust, honesty and integrity within teams. Armed forces personnel must communicate really difficult messages. Telling people that many of them may die within hours demands a harsh honesty, but it builds trust. Combine this with an ability to achieve shared goals, and military leaders inspire others to follow them regardless of the obstacles. So veterans bring blunt honesty, communication, and a mission focus to do what is needed to succeed. These are all characteristics that are essential in cybersecurity, where you have to call out critical risks that others might avoid discussing.Reclaiming the Architect’s Role in the SDLC
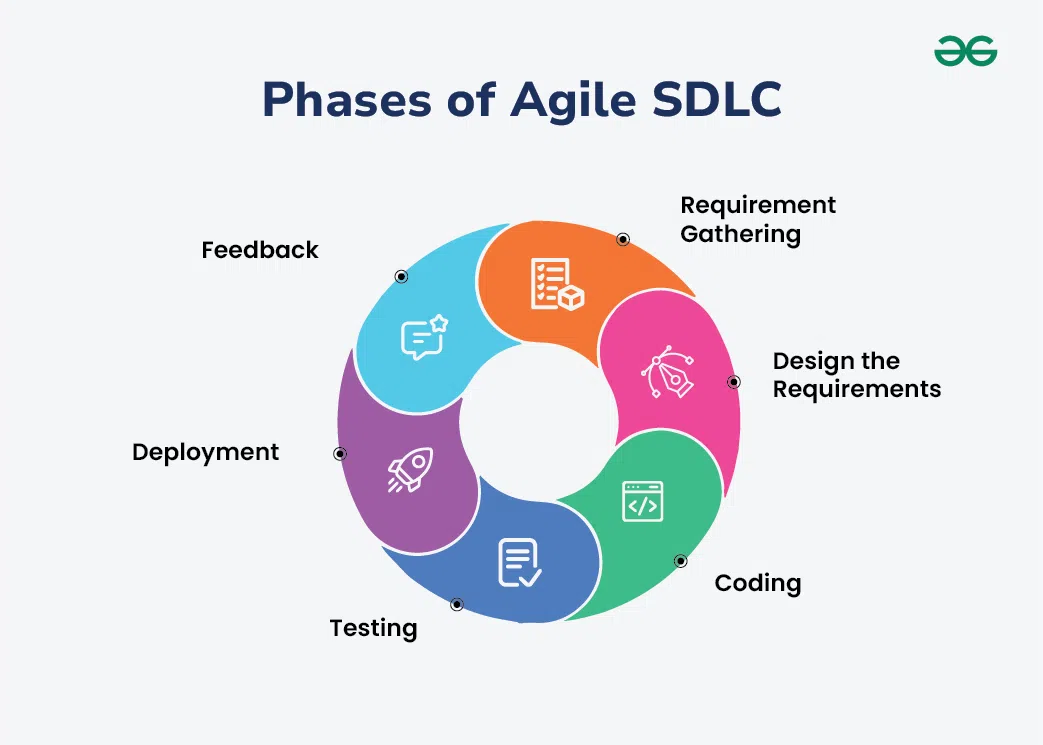 Without an active architect guiding the design and implementation, systems can
experience architectural drift, a term that describes the gradual divergence
from the intended system design, leading to a fragmented and harder-to-manage
system. In the absence of architectural oversight, development teams may
optimize for individual tasks at the expense of the system’s overall
performance, scalability, and maintainability. ... The architect is primarily
accountable for the overall design and ensuring the system’s quality,
performance, scalability, and adaptability to meet changing demands. However,
relying on outdated practices, like manually written and updated design
documents, is no longer effective. The modern software landscape, with multiple
services, external resources, and off-the-shelf integrations, makes such
documents stale almost as soon as they’re written. Consequently, architects must
use automated tools to document and monitor live system architectures. These
tools can help architects identify potential issues almost in real time, which
allows them to proactively address problems and ensure design integrity
throughout the development process. These tools are especially useful in the
design stage, allowing architects to reclaim the role they once possessed and
the responsibilities that come with it.
Without an active architect guiding the design and implementation, systems can
experience architectural drift, a term that describes the gradual divergence
from the intended system design, leading to a fragmented and harder-to-manage
system. In the absence of architectural oversight, development teams may
optimize for individual tasks at the expense of the system’s overall
performance, scalability, and maintainability. ... The architect is primarily
accountable for the overall design and ensuring the system’s quality,
performance, scalability, and adaptability to meet changing demands. However,
relying on outdated practices, like manually written and updated design
documents, is no longer effective. The modern software landscape, with multiple
services, external resources, and off-the-shelf integrations, makes such
documents stale almost as soon as they’re written. Consequently, architects must
use automated tools to document and monitor live system architectures. These
tools can help architects identify potential issues almost in real time, which
allows them to proactively address problems and ensure design integrity
throughout the development process. These tools are especially useful in the
design stage, allowing architects to reclaim the role they once possessed and
the responsibilities that come with it.
Is Vibe Coding Ready for Prime Time?
As the vibe coding ecosystem matures, AI coding platforms are rolling out safeguards like dev/prod separation, backups/rollback, single sign-on, and SOC 2 reporting, yet audit logging is still not uniform across tools. But until these enterprise-grade controls become standard, organizations must proactively build their own guardrails to ensure AI-generated code remains secure, scalable and trustworthy. This calls for a risk-based approach, one that adjusts oversight based on the likelihood and impact of potential risks. Not all use cases carry the same weight. Some are low-stakes and well-suited for experimentation, while others may introduce serious security, regulatory or operational risks. By focusing controls where they’re most needed, a risk-based approach helps protect critical systems while still enabling speed and innovation in safer contexts. ... To effectively manage the risks of vibe coding, teams need to ask targeted questions that reflect the unique challenges of AI-generated code. These questions help determine how much oversight is needed and whether vibe coding is appropriate for the task at hand. ... Vibe coding unlocks new ways of thinking for software development. However, it also shifts risk upstream. The speed of code generation doesn’t eliminate the need for review, control and accountability. In fact, it makes those even more important.7 reasons the SOC is in crisis — and 5 steps to fix it
 The problem is that our systems verify accounts, not actual people. Once an
attacker assumes a user’s identity through social engineering, they can often
operate within normal parameters for extended periods. Most detection systems
aren’t sophisticated enough to recognise that John Doe’s account is being used
by someone who isn’t actually John Doe. ... In large enterprises with organic
system growth, different system owners, legacy environments, and shadow SaaS
integrations, misconfigurations are inevitable. No vulnerability scanner will
flag identity systems configured inconsistently across domains, cloud services
with overly permissive access policies, or network segments that bypass security
controls. These misconfigurations often provide attackers with the lateral
movement opportunities they need once they’ve gained initial access through
compromised credentials. Yet most organizations have no systematic approach to
identifying and remediating these architectural weaknesses. ... External SOC
providers offer round-the-clock monitoring and specialised expertise, but they
lack the organizational context that makes detection effective. They don’t
understand your business processes, can’t easily distinguish between legitimate
and suspicious activities, and often lack the authority to take decisive action.
The problem is that our systems verify accounts, not actual people. Once an
attacker assumes a user’s identity through social engineering, they can often
operate within normal parameters for extended periods. Most detection systems
aren’t sophisticated enough to recognise that John Doe’s account is being used
by someone who isn’t actually John Doe. ... In large enterprises with organic
system growth, different system owners, legacy environments, and shadow SaaS
integrations, misconfigurations are inevitable. No vulnerability scanner will
flag identity systems configured inconsistently across domains, cloud services
with overly permissive access policies, or network segments that bypass security
controls. These misconfigurations often provide attackers with the lateral
movement opportunities they need once they’ve gained initial access through
compromised credentials. Yet most organizations have no systematic approach to
identifying and remediating these architectural weaknesses. ... External SOC
providers offer round-the-clock monitoring and specialised expertise, but they
lack the organizational context that makes detection effective. They don’t
understand your business processes, can’t easily distinguish between legitimate
and suspicious activities, and often lack the authority to take decisive action.
One Network: Cloud-Agnostic Service and Policy-Oriented Network Architecture
/filters:no_upscale()/articles/one-network-service-policy-architecture/en/resources/103figure-2-1754550912924.jpg) The goal of One Network is to enable uniform policies across services. To do so,
we are looking to overcome the complexities of heterogeneous networking,
different language runtimes, and the coexistence of monolith services and
microservices. These complexities span multiple environments, including public,
private, and multi-cloud setups. The idea behind One Network is to simplify the
current state of affairs by asking, "Why do I need so many networks? Can I have
one network?" ... One Network enables you to manage such a service by applying
governance, orchestrating policy, and managing the small independent services.
Each of these microservices is imagined as a service endpoint. This enables
orchestrating and grouping these service endpoints without application
developers needing to modify service implementation, so everything is done on a
network. There are three ways to manage these service endpoints. The first is
the classic model: you add a load balancer before a workload, such as a shopping
cart service running in multiple regions, and that becomes your service
endpoint. ... If you start with a flat network but want to create boundaries,
you can segment by exposing only certain services and keeping others
hidden.
The goal of One Network is to enable uniform policies across services. To do so,
we are looking to overcome the complexities of heterogeneous networking,
different language runtimes, and the coexistence of monolith services and
microservices. These complexities span multiple environments, including public,
private, and multi-cloud setups. The idea behind One Network is to simplify the
current state of affairs by asking, "Why do I need so many networks? Can I have
one network?" ... One Network enables you to manage such a service by applying
governance, orchestrating policy, and managing the small independent services.
Each of these microservices is imagined as a service endpoint. This enables
orchestrating and grouping these service endpoints without application
developers needing to modify service implementation, so everything is done on a
network. There are three ways to manage these service endpoints. The first is
the classic model: you add a load balancer before a workload, such as a shopping
cart service running in multiple regions, and that becomes your service
endpoint. ... If you start with a flat network but want to create boundaries,
you can segment by exposing only certain services and keeping others
hidden.
Excellent articles and quick read for cyber professional
ReplyDelete