A number of blockchain startups are working on tokenizing real estate ownership to overcome these challenges and open real estate investment to more people. An example is BitProperty, a platform that enables property owners to register their property on the blockchain and issue tokens, digital currencies that represent a share of their property. When a person wants to invest in the property, they can purchase any number of its corresponding tokens on BitProperty. Contractors and construction companies can use the BitProperty to raise funds for their projects by launching initial coin offerings (ICO). Anyone who wants to invest in the project can purchase the project’s tokens. In return, they’ll have proportional share of the value and revenue of the finished project in the future.
For a time, Linux OS computers were expected to become the dominant third player in the PC market, Huang said. For example, many thought Linux would be the ideal OS for netbooks, which peaked in popularity in the late 2000s/early 2010s. But Microsoft captured that market by “bottom-ending” Windows to run on the low-powered portables. There’s still talk that Linux could emerge as the dominant OS for thin clients. But IDC’s data doesn’t support that belief. Linux comprised a 3% share of global PC shipments in 2013, but it’s held steady at a mere 1% since 2015 and is expected to stay at 1% through 2021. By comparison, Chrome OS has risen from 1% of the market in 2013 to its current position of 5.5% in 2017, and IDC expects it to reach 8% by 2021.
The vulnerabilities stakeholders face include cyber security, data privacy, data breaches, and payments fraud. The utmost vigilance is required to protect organisations against cyber attacks and all stakeholders, including regulators, must be more proactive regarding cybersecurity, with ownership of the issue taken to prevent attacks. In the new payments ecosystem, third-party developers can directly interact with a partner banks’ customers, raising questions about data privacy and security. In an increasingly networked ecosystem, identifying the source of attack will be a challenge. Verizon’s 2017 Data Breach Investigations Report found that security incidents and data breaches affect both large and small financial organisations almost equally. However, the security of larger banks is difficult to compromise as they invest more in cyber security solutions. Smaller banks, which do not have the same access to resources, are more prone to cyberattacks.
A soon-to-be published study shows how the traditional corporate human resources operation actually hampers cybersecurity hiring against a backdrop of the industry's well-documented talent gap. The Jane Bond Project report, commissioned by security talent recruiting firm CyberSN, found that in addition to the lack of available talent for those positions, respondents say their HR generalists are not equipped to recruit and hire cybersecurity talent, and that flawed salary data complicates their ability to issue the best job offers. More than 80% of the 83 cybersecurity positions studied in the report ended up with compensation offers higher than the salary caps stated in the original job descriptions. Half of the 52 organizations participating in the study say they had to up the compensation offers to seal the deal. The positions in the study include security engineers, product sales engineers, incident response analysts, SOC analysts, and product security experts.
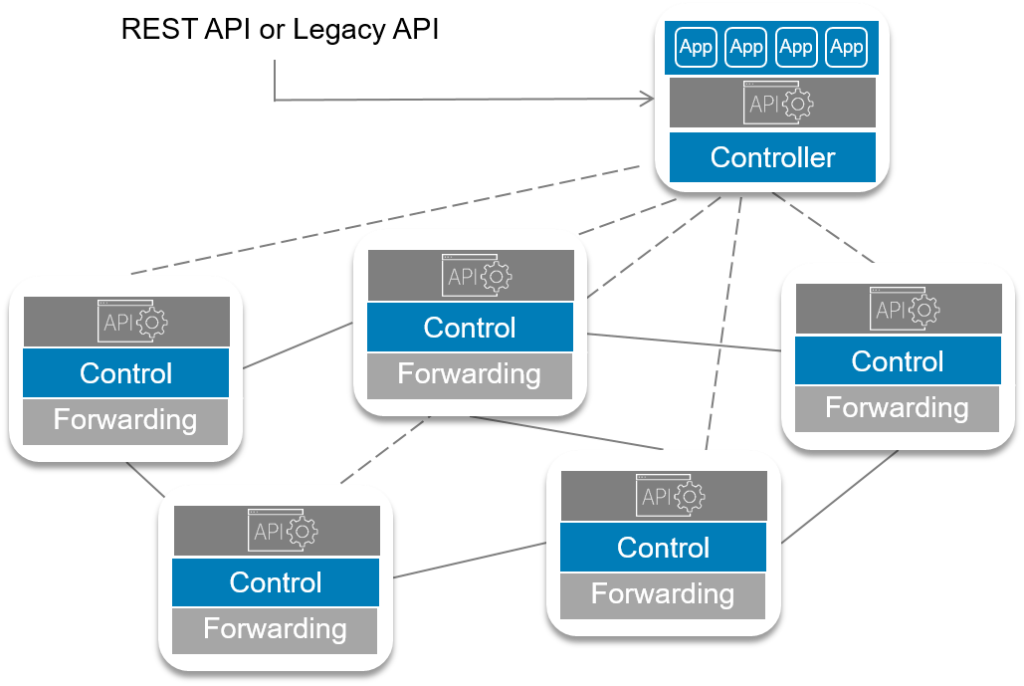
Obviously, no company is going to replace all of their hardware overnight, as it would require considerable expense, implementation and architecture challenges that, until resolved, could impact company operations. In addition, there would be plenty of non- technical issues, like employees knowing device X and networkOSY like the palm of their hands and not looking forward to the time it might take to learn new technology and processes. When a company decides to transform to a software defined networking infrastructure, they may not get support from their existing Network hardware vendor, which might beenjoying hefty margins in network hardware sales, not thrilled to push a technology that will make their expensive boxes replaceable for cheap vendor agnostic white boxes.
According to Badman, Extreme's Automated Campus initiative shows great promise due, in part, to 802.1aq shortest path bridging, which supplants routing protocols such as Border Gateway Protocol (BGP), MPLS and Open Shortest Path First (OSPF), thereby reducing complexity. The new network fabric also includes hypersegmentation to contain security breaches, APIs to increase interoperability, and user and device policies that drive automated network changes in conjunction with analytics and changes on the edge. Badman said he views Avaya as one of the leaders of software-defined networking fabrics, adding that Extreme has succeeded in integrating Avaya fabrics since it acquired the vendor. "I'm of the opinion that some vendors are trying to figure out how to proceed with network-wide fabric methods, while painting beta-grade efforts up with glitz and catchy slogans. This just isn't the case for Extreme," he wrote.

Despite having capable teams of programmers and rigorous testing procedures, many companies – be they retailers, manufacturers, or service providers – still have a hard time seeing the potential vulnerabilities in their own systems. “There are a lot of companies who think ‘this will never happen’ and then they come back to us six months later saying ‘it happened’,” says Kupev. The challenge, he explains, is being able to look at things from a different point of view. “Often a client’s view of things can be quite narrow because they’re used to looking at things from the same perspective,” he adds. “Our job is to help them look at matters from a different angle and uncover vulnerabilities they would have otherwise missed.” To illustrate his point, Kupev tells the story of an engine maker that invested heavily in ensuring a device’s “regular” communications systems are secure.
The ability to decrypt packets can be used to decrypt TCP SYN packets. This allows an adversary to obtain the TCP sequence numbers of a connection, and hijack TCP connections. As a result, even though WPA2 is used, the adversary can now perform one of the most common attacks against open Wi-Fi networks: injecting malicious data into unencrypted HTTP connections. For example, an attacker can abuse this to inject ransomware or malware into websites that the victim is visiting. If the victim uses either the WPA-TKIP or GCMP encryption protocol, instead of AES-CCMP, the impact is especially catastrophic.Against these encryption protocols, nonce reuse enables an adversary to not only decrypt, but also to forge and inject packets. Moreover, because GCMP uses the same authentication key in both communication directions, and this key can be recovered if nonces are reused, it is especially affected.

Metered DDoS pricing used to be more common, said Theresa Abbamondi, director of product management for Arbor Cloud and Services at Arbor Networks, Inc. That created a risk for customers, she said. Arbor has been pricing based on clean traffic when it launched its service four years ago, one of the first vendors to do so. "Most of the purpose-build anti-DDoS vendors quickly moved to this type of clean traffic pricing model, and it became the standard in the high end of the market," she said. "Among vendors like Cloudflare, who sell DDoS as an add-on service to a customer base more interested in the vendor’s core offerings, it’s still common today to see vendors limiting the total bandwidth of traffic they will scrub, blackholing traffic that exceeds that threshold, or hitting the customer with exorbitant, hidden fees," said Abbamondi.
New derived credential technology eliminates the need for a physical card by placing verified identity credentials directly and securely onto the mobile device, much as mobile-pay systems do away with the need to make payments using a plastic credit card. This technology offers the added benefits of making identity verification more convenient, and preventing unauthorized logins. But derived credentials and authentication tools such as biometrics offer only a one-time, “snapshot” form of user verification. Once the user has passed the initial test and gained access, the device and everything on it become fully available for viewing and use. Behavioral analytics promises to change this paradigm. ... tools designed to capture how a device is used can provide the equivalent of a continuously-authenticating security “video,” to detect interlopers, transaction by transaction.
Quote for the day:
"Anger is the feeling that makes your mouth work faster than your mind." -- Evan Esar

No comments:
Post a Comment