Quote for the day:
“Our chief want is someone who will inspire us to be what we know we could be.” -- Ralph Waldo Emerson
A Brief History of GPT Through Papers
 The first neural network based language translation models operated in three
steps (at a high level). An encoder would embed the “source statement” into a
vector space, resulting in a “source vector”. Then, the source vector would be
mapped to a “target vector” through a neural network and finally a decoder would
map the resulting vector to the “target statement”. People quickly realized that
the vector that was supposed to encode the source statement had too much
responsibility. The source statement could be arbitrarily long. So, instead of a
single vector for the entire statement, let’s convert each word into a vector
and then have an intermediate element that would pick out the specific words
that the decoder should focus more on. ... The mechanism by which the words were
converted to vectors was based on recurrent neural networks (RNNs). Details of
this can be obtained from the paper itself. These recurrent neural networks
relied on hidden states to encode the past information of the sequence. While
it’s convenient to have all that information encoded into a single vector, it’s
not good for parallelizability since that vector becomes a bottleneck and must
be computed before the rest of the sentence can be processed. ... The idea is to
give the model demonstrative examples at inference time as opposed to using them
to train its parameters. If no such examples are provided in-context, it is
called “zero shot”. If one example is provided, “one shot” and if a few are
provided, “few shot”.
The first neural network based language translation models operated in three
steps (at a high level). An encoder would embed the “source statement” into a
vector space, resulting in a “source vector”. Then, the source vector would be
mapped to a “target vector” through a neural network and finally a decoder would
map the resulting vector to the “target statement”. People quickly realized that
the vector that was supposed to encode the source statement had too much
responsibility. The source statement could be arbitrarily long. So, instead of a
single vector for the entire statement, let’s convert each word into a vector
and then have an intermediate element that would pick out the specific words
that the decoder should focus more on. ... The mechanism by which the words were
converted to vectors was based on recurrent neural networks (RNNs). Details of
this can be obtained from the paper itself. These recurrent neural networks
relied on hidden states to encode the past information of the sequence. While
it’s convenient to have all that information encoded into a single vector, it’s
not good for parallelizability since that vector becomes a bottleneck and must
be computed before the rest of the sentence can be processed. ... The idea is to
give the model demonstrative examples at inference time as opposed to using them
to train its parameters. If no such examples are provided in-context, it is
called “zero shot”. If one example is provided, “one shot” and if a few are
provided, “few shot”.8 Powerful Lessons from Robert Herjavec at Entrepreneur Level Up That Every Founder Needs to Hear
Entrepreneurs who remain curious — asking questions and seeking insights —
often discover pathways others overlook. Instead of dismissing a "no" or a
difficult response, Herjavec urged attendees to look for the opportunity
behind it. Sometimes, the follow-up question or the willingness to listen more
deeply is what transforms rejection into possibility. ... while breakthrough
innovations capture headlines, the majority of sustainable businesses are
built on incremental improvements, better execution and adapting existing
ideas to new markets. For entrepreneurs, this means it's okay if your business
doesn't feel revolutionary from day one. What matters is staying committed to
evolving, improving and listening to the market. ... setbacks are inevitable
in entrepreneurship. The real test isn't whether you'll face challenges, but
how you respond to them. Entrepreneurs who can adapt — whether by shifting
strategy, reinventing a product or rethinking how they serve customers — are
the ones who endure. ... when leaders lose focus, passion or clarity, the
organization inevitably follows. A founder's vision and energy cascade down
into the culture, decision-making and execution. If leaders drift, so does the
company. For entrepreneurs, this is a call to self-reflection. Protect your
clarity of purpose. Revisit why you started. And remember that your team looks
to you not just for direction, but for inspiration.
The era of cheap AI coding assistants may be over
 Developers have taken to social media platforms and GitHub to express their
dissatisfaction over the pricing changes, especially across tools like Claude
Code, Kiro, and Cursor, but vendors have not adjusted pricing or made any
changes that significantly reduce credits consumption. Analysts don’t see any
alternative to reducing the pricing of these tools. "There’s really no
alternative until someone figures out the following: how to use cheaper but
dumber models than Claude Sonnet 4 to achieve the same user experience and
innovate on KVCache hit rate to reduce the effective price per dollar,” said Wei
Zhou, head of AI utility research at SemiAnalysis. Considering the market
conditions, CIOs and their enterprises need to start absorbing the cost and
treat vibe coding tools as a productivity expense, according to Futurum’s
Hinchcliffe. “CIOs should start allocating more budgets for vibe coding tools,
just as they would do for SaaS, cloud storage, collaboration tools or any other
line items,” Hinchcliffe said. “The case of ROI on these tools is still strong:
faster shipping, fewer errors, and higher developer throughput. Additionally, a
good developer costs six figures annually, while vibe coding tools are still
priced in the low-to-mid thousands per seat,” Hinchcliffe added. ...
“Configuring assistants to intervene only where value is highest and choosing
smaller, faster models for common tasks and saving large-model calls for edge
cases could bring down expenditure,” Hinchcliffe added.
Developers have taken to social media platforms and GitHub to express their
dissatisfaction over the pricing changes, especially across tools like Claude
Code, Kiro, and Cursor, but vendors have not adjusted pricing or made any
changes that significantly reduce credits consumption. Analysts don’t see any
alternative to reducing the pricing of these tools. "There’s really no
alternative until someone figures out the following: how to use cheaper but
dumber models than Claude Sonnet 4 to achieve the same user experience and
innovate on KVCache hit rate to reduce the effective price per dollar,” said Wei
Zhou, head of AI utility research at SemiAnalysis. Considering the market
conditions, CIOs and their enterprises need to start absorbing the cost and
treat vibe coding tools as a productivity expense, according to Futurum’s
Hinchcliffe. “CIOs should start allocating more budgets for vibe coding tools,
just as they would do for SaaS, cloud storage, collaboration tools or any other
line items,” Hinchcliffe said. “The case of ROI on these tools is still strong:
faster shipping, fewer errors, and higher developer throughput. Additionally, a
good developer costs six figures annually, while vibe coding tools are still
priced in the low-to-mid thousands per seat,” Hinchcliffe added. ...
“Configuring assistants to intervene only where value is highest and choosing
smaller, faster models for common tasks and saving large-model calls for edge
cases could bring down expenditure,” Hinchcliffe added.AI agents need intent-based blockchain infrastructure
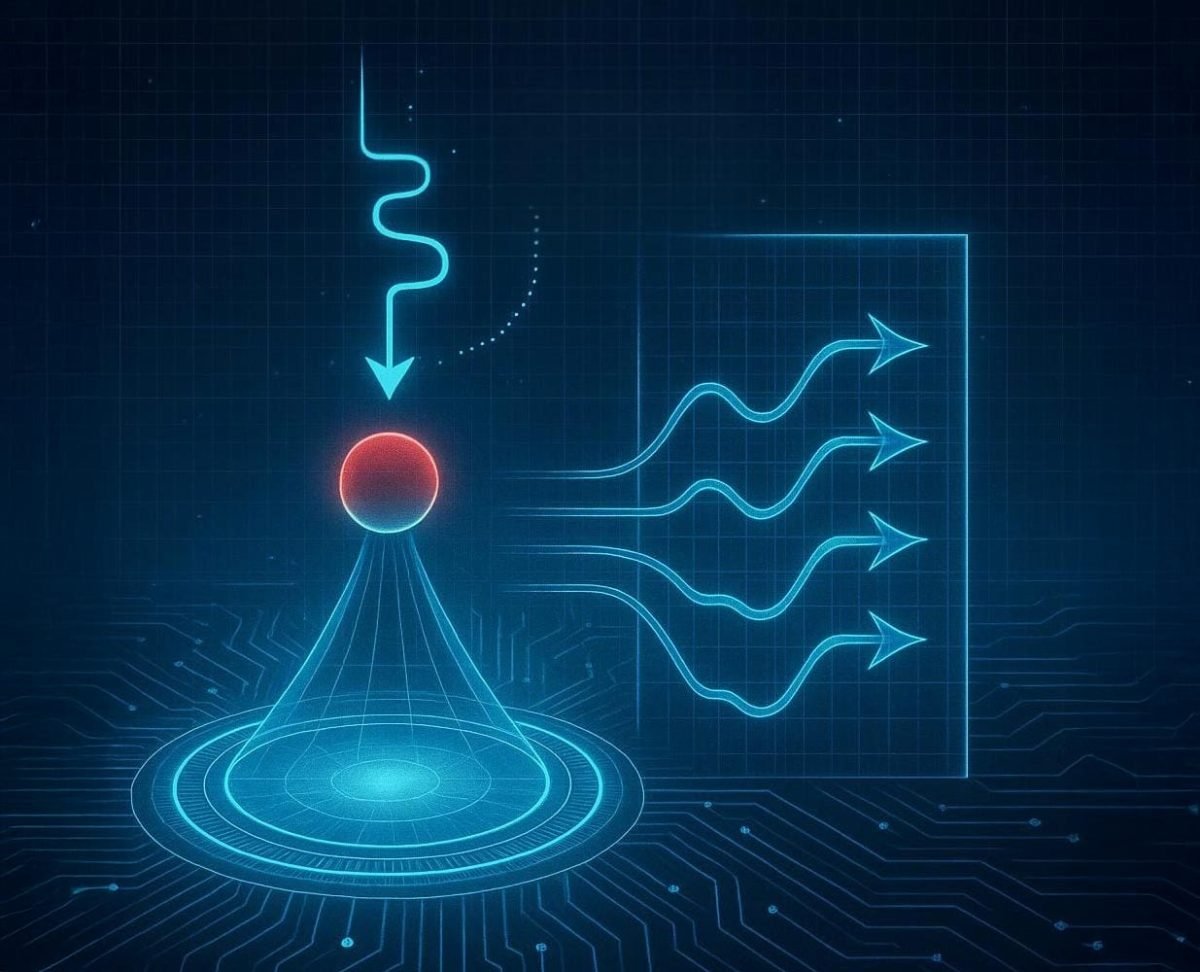
 By integrating agents with intent-centric systems, however, we can ensure users
fully control their data and assets. Intents are a type of building block for
decentralized applications that give users complete control over the outcome of
their transactions. Powered by a decentralized network of solvers, agentic nodes
that compete to solve user transactions, these systems eliminate the complexity
of the blockchain experience while maintaining user sovereignty and privacy
throughout the process. ... Combining AI agents and intents will redefine the
Web3 experience while keeping the space true to its core values. Intents bridge
users and agents, ensuring the UX benefits users expect from AI while
maintaining decentralization, sovereignty and verifiability. Intent-based
systems will play a crucial role in the next phase of Web3’s evolution by
ensuring agents act in users’ best interests. As AI adoption grows, so does the
risk of replicating the problems of Web2 within Web3. Intent-centric
infrastructure is the key to addressing both the challenges and opportunities
that AI agents bring and is necessary to unlock their full potential. Intents
will be an essential infrastructure component and a fundamental requirement for
anyone integrating or considering integrating AI into DeFi. Intents are not
merely a type of UX upgrade or optional enhancement.
By integrating agents with intent-centric systems, however, we can ensure users
fully control their data and assets. Intents are a type of building block for
decentralized applications that give users complete control over the outcome of
their transactions. Powered by a decentralized network of solvers, agentic nodes
that compete to solve user transactions, these systems eliminate the complexity
of the blockchain experience while maintaining user sovereignty and privacy
throughout the process. ... Combining AI agents and intents will redefine the
Web3 experience while keeping the space true to its core values. Intents bridge
users and agents, ensuring the UX benefits users expect from AI while
maintaining decentralization, sovereignty and verifiability. Intent-based
systems will play a crucial role in the next phase of Web3’s evolution by
ensuring agents act in users’ best interests. As AI adoption grows, so does the
risk of replicating the problems of Web2 within Web3. Intent-centric
infrastructure is the key to addressing both the challenges and opportunities
that AI agents bring and is necessary to unlock their full potential. Intents
will be an essential infrastructure component and a fundamental requirement for
anyone integrating or considering integrating AI into DeFi. Intents are not
merely a type of UX upgrade or optional enhancement.
The future of software development: To what can AI replace human developers?
 Rather than replacing developers, AI is transforming them into higher-level
orchestrators of technology. The emerging model is one of human-AI
collaboration, where machines handle the repetitive scaffolding and humans focus
on design, strategy, and oversight. In this new world, developers must learn not
just to write code, but to guide, prompt, and supervise AI systems. The skillset
is expanding from syntax and logic to include abstraction, ethical reasoning,
systems thinking, and interdisciplinary collaboration. In other words, AI is not
making developers obsolete. It is making new demands on their expertise. ...
This shift has significant implications for how we educate the next generation
of software professionals. Beyond coding languages, students will need to
understand how to evaluate AI- AI-generated output, how to embed ethical
standards into automated systems, and how to lead hybrid teams made up of both
humans and machines. It also affects how organisations hire and manage talent.
Companies must rethink job descriptions, career paths, and performance metrics
to account for the impact of AI-enabled development. Leaders must focus on AI
literacy, not just technical competence. Professionals seeking to stay ahead of
the curve can explore free programs, such as The Future of Software Engineering
Led by Emerging Technologies, which introduces the evolving role of AI in modern
software development.
Rather than replacing developers, AI is transforming them into higher-level
orchestrators of technology. The emerging model is one of human-AI
collaboration, where machines handle the repetitive scaffolding and humans focus
on design, strategy, and oversight. In this new world, developers must learn not
just to write code, but to guide, prompt, and supervise AI systems. The skillset
is expanding from syntax and logic to include abstraction, ethical reasoning,
systems thinking, and interdisciplinary collaboration. In other words, AI is not
making developers obsolete. It is making new demands on their expertise. ...
This shift has significant implications for how we educate the next generation
of software professionals. Beyond coding languages, students will need to
understand how to evaluate AI- AI-generated output, how to embed ethical
standards into automated systems, and how to lead hybrid teams made up of both
humans and machines. It also affects how organisations hire and manage talent.
Companies must rethink job descriptions, career paths, and performance metrics
to account for the impact of AI-enabled development. Leaders must focus on AI
literacy, not just technical competence. Professionals seeking to stay ahead of
the curve can explore free programs, such as The Future of Software Engineering
Led by Emerging Technologies, which introduces the evolving role of AI in modern
software development.Open Data Fabric: Rethinking Data Architecture for AI at Scale
The first principle, unified data access, ensures that agents have federated real-time access across all enterprise data sources without requiring pipelines, data movement, or duplication. Unlike human users who typically work within specific business domains, agents often need to correlate information across the entire enterprise to generate accurate insights. ... The second principle, unified contextual intelligence, involves providing agents with the business and technical understanding to interpret data correctly. This goes far beyond traditional metadata management to include business definitions, domain knowledge, usage patterns, and quality indicators from across the enterprise ecosystem. Effective contextual intelligence aggregates information from metadata, data catalogs, business glossaries, business intelligence tools, and tribal knowledge into a unified layer that agents can access in real-time. ... Perhaps the most significant principle involves establishing collaborative self-service. This is a significant shift as it means moving from static dashboards and reports to dynamic, collaborative data products and insights that agents can generate and share with each other. The results are trusted “data answers,” or conversational, on-demand data products for the age of AI that include not just query results but also the business context, methodology, lineage, and reasoning that went into generating them.A Simple Shift in Light Control Could Revolutionize Quantum Computing
 A research collaboration led by Vikas Remesh of the Photonics Group at the
Department of Experimental Physics, University of Innsbruck, together with
partners from the University of Cambridge, Johannes Kepler University Linz, and
other institutions, has now demonstrated a way to bypass these challenges. Their
method relies on a fully optical process known as stimulated two-photon
excitation. This technique allows quantum dots to emit streams of photons in
distinct polarization states without the need for electronic switching hardware.
In tests, the researchers successfully produced high-quality two-photon states
while maintaining excellent single-photon characteristics. ... “The method works
by first exciting the quantum dot with precisely timed laser pulses to create a
biexciton state, followed by polarization-controlled stimulation pulses that
deterministically trigger photon emission in the desired polarization,” explain
Yusuf Karli and Iker Avila Arenas, the study’s first authors. ... “What makes
this approach particularly elegant is that we have moved the complexity from
expensive, loss-inducing electronic components after the single photon emission
to the optical excitation stage, and it is a significant step forward in making
quantum dot sources more practical for real-world applications,” notes Vikas
Remesh, the study’s lead researcher.
A research collaboration led by Vikas Remesh of the Photonics Group at the
Department of Experimental Physics, University of Innsbruck, together with
partners from the University of Cambridge, Johannes Kepler University Linz, and
other institutions, has now demonstrated a way to bypass these challenges. Their
method relies on a fully optical process known as stimulated two-photon
excitation. This technique allows quantum dots to emit streams of photons in
distinct polarization states without the need for electronic switching hardware.
In tests, the researchers successfully produced high-quality two-photon states
while maintaining excellent single-photon characteristics. ... “The method works
by first exciting the quantum dot with precisely timed laser pulses to create a
biexciton state, followed by polarization-controlled stimulation pulses that
deterministically trigger photon emission in the desired polarization,” explain
Yusuf Karli and Iker Avila Arenas, the study’s first authors. ... “What makes
this approach particularly elegant is that we have moved the complexity from
expensive, loss-inducing electronic components after the single photon emission
to the optical excitation stage, and it is a significant step forward in making
quantum dot sources more practical for real-world applications,” notes Vikas
Remesh, the study’s lead researcher.AI and the New Rules of Observability
The gap between "monitoring" and true observability is both cultural and technological. Enterprises haven't matured beyond monitoring because old tools weren't built for modern systems, and organizational cultures have been slow to evolve toward proactive, shared ownership of reliability. ... One blind spot is model drift, which occurs when data shifts, rendering its assumptions invalid. In 2016, Microsoft's Tay chatbot was a notable failure due to its exposure to shifting user data distributions. Infrastructure monitoring showed uptime was fine; only semantic observability of outputs would have flagged the model's drift into toxic behavior. Hidden technical debt or unseen complexity in code can undermine observability. In machine learning, or ML, systems, pipelines often fail silently, while retraining processes, feature pipelines and feedback loops create fragile dependencies that traditional monitoring tools may overlook. Another issue is "opacity of predictions." ... AI models often learn from human-curated priorities. If ops teams historically emphasized CPU or network metrics, the AI may overweigh those signals while downplaying emerging, equally critical patterns - for example, memory leaks or service-to-service latency. This can occur as bias amplification, where the model becomes biased toward "legacy priorities" and blind to novel failure modes. Bias often mirrors reality.Dynamic Integration for AI Agents – Part 1
 An integration of components within AI differs from an integration between AI
agents. The former relates to integration with known entities that form a
deterministic model of information flow. The same relates to inter-application,
inter-system and inter-service transactions required by a business process at
large. It is based on mapping of business functionality and information (an
architecture of the business in organisations) onto available IT systems,
applications, and services. The latter shifts the integration paradigm since the
very AI Agents decide that they need to integrate with something at runtime
based on the overlapping of the statistical LLM and available information, which
contains linguistic ties unknown even in the LLM training. That is, an AI Agent
does not know what a counterpart — an application, another AI Agent or data
source — it would need to cooperate with to solve the overall task given to it
by its consumer/user. The AI Agent does not know even if the needed counterpart
exists. ... Any AI Agent may have its individual owner and provider. These
owners and providers may be unaware of each others and act independently when
creating their AI Agents. No AI Agent can be self-sufficient due to its
fundamental design — it depends on the prompts and real-world data at runtime.
It seems that the approaches to integration and the integration solutions differ
for the humanitarian and natural science spheres.
An integration of components within AI differs from an integration between AI
agents. The former relates to integration with known entities that form a
deterministic model of information flow. The same relates to inter-application,
inter-system and inter-service transactions required by a business process at
large. It is based on mapping of business functionality and information (an
architecture of the business in organisations) onto available IT systems,
applications, and services. The latter shifts the integration paradigm since the
very AI Agents decide that they need to integrate with something at runtime
based on the overlapping of the statistical LLM and available information, which
contains linguistic ties unknown even in the LLM training. That is, an AI Agent
does not know what a counterpart — an application, another AI Agent or data
source — it would need to cooperate with to solve the overall task given to it
by its consumer/user. The AI Agent does not know even if the needed counterpart
exists. ... Any AI Agent may have its individual owner and provider. These
owners and providers may be unaware of each others and act independently when
creating their AI Agents. No AI Agent can be self-sufficient due to its
fundamental design — it depends on the prompts and real-world data at runtime.
It seems that the approaches to integration and the integration solutions differ
for the humanitarian and natural science spheres.Counteracting Cyber Complacency: 6 Security Blind Spots for Credit Unions
 Organizations that conduct only basic vendor vetting lack visibility into the
cybersecurity practices of their vendors’ subcontractors. This creates gaps in
oversight that attackers can exploit to gain access to an institution’s data.
Third-party providers often have direct access to critical systems, making them
an attractive target. When they’re compromised, the consequences quickly extend
to the credit unions they serve. ... Cybercriminals continue to exploit employee
behavior as a primary entry point into financial institutions. Social
engineering tactics — such as phishing, vishing, and impersonation — bypass
technical safeguards by manipulating people. These attacks rely on trust,
familiarity, or urgency to provoke an action that grants the attacker access to
credentials, systems, or internal data. ... Many credit unions deliver
cybersecurity training on an annual schedule or only during onboarding. These
programs often lack depth, fail to differentiate between job functions, and lose
effectiveness over time. When training is overly broad or infrequent, staff and
leadership alike may be unprepared to recognize or respond to threats. The risk
is heightened when the threats are evolving faster than the curriculum. TruStage
advises tailoring cyber education to the institution’s structure and risk
profile. Frontline staff who manage member accounts face different risks than
board members or vendors.
Organizations that conduct only basic vendor vetting lack visibility into the
cybersecurity practices of their vendors’ subcontractors. This creates gaps in
oversight that attackers can exploit to gain access to an institution’s data.
Third-party providers often have direct access to critical systems, making them
an attractive target. When they’re compromised, the consequences quickly extend
to the credit unions they serve. ... Cybercriminals continue to exploit employee
behavior as a primary entry point into financial institutions. Social
engineering tactics — such as phishing, vishing, and impersonation — bypass
technical safeguards by manipulating people. These attacks rely on trust,
familiarity, or urgency to provoke an action that grants the attacker access to
credentials, systems, or internal data. ... Many credit unions deliver
cybersecurity training on an annual schedule or only during onboarding. These
programs often lack depth, fail to differentiate between job functions, and lose
effectiveness over time. When training is overly broad or infrequent, staff and
leadership alike may be unprepared to recognize or respond to threats. The risk
is heightened when the threats are evolving faster than the curriculum. TruStage
advises tailoring cyber education to the institution’s structure and risk
profile. Frontline staff who manage member accounts face different risks than
board members or vendors.
No comments:
Post a Comment