Suspected MFA Bombing Attacks Target Apple iPhone Users

Multifactor bombing attacks — also known as multifactor fatigue attacks — are a
social engineering exploit in which attackers flood a target's phone, computer,
or email account with push notifications to approve a login or a password reset.
The idea behind these attacks is to overwhelm a target with so many
second-factor authentication requests that they eventually accept one either
mistakenly or because they want the notifications to stop. Typically, these
attacks have involved the threat actors first illegally obtaining the username
and password to a victim account and then using a bombing or fatigue attack to
obtain second-factor authentication to accounts protected by MFA. In 2022, for
instance, members of the Lapsus$ threat group obtained the VPN credentials for
an individual working for a third-party contractor for Uber. They then used the
credentials to repeatedly try and log in to the contractor's VPN account
triggering a two-factor authentication request on the contractor's phone each
time — which the contractor ultimately approved. The attackers then used the VPN
access to breach multiple Uber systems.
Finding software flaws early in the development process provides ROI
Unfortunately, enterprise software development teams at many organizations are
not finding security-related software flaws as they write their software. As a
result, such flaws get shipped in the applications used by customers, partners,
suppliers, and employees. This creates serious security risks as threat actors
might find and use these flaws to breach enterprise applications and move
laterally throughout their target environments. Once a security-related flaw is
published to software used in production, the race is on to find the bug first.
If a company is lucky, the flaw will be found during a software security
assessment by its internal security team or perhaps a third-party provider. If
the flaw lingers too long, it’s more likely to be found by an attacker targeting
the organization in the hopes of stealing data or perhaps conducting a
ransomware attack. The security and increased trust associated with quality
software are clear. The return on investment and the business benefits of
high-quality and secure software are not always well understood.
7 tips for leading without authority

Leading without authority starts with individuals deciding to create change then
bringing people together over a shared goal. If you believe in this strategy and
want it to work, make it fundamental to your organizational structure. “We made
an intentional transition at the onset of the pandemic to be a fully remote
organization,” says Elaine Mak, chief people and performance officer at
Valimail. “At the same time, we transitioned from a founder-led to a team-led
model.” That transition involved democratizing decision-making, relying on
experts within the organization, and leaning into letting people create outcomes
through collaboration. “I brought the phrase, ‘Don’t be right, get it right,’
into the organization,” says Seth Blank, Valimail’s CTO. “It’s at the crux of
the question of how to lead without authority. If you’re the expert and you
bring a team together, come in with humility and ask, ‘How do we do this? How do
we learn together?’ If you do that, you can move mountains from anywhere on the
organization — if the organization is set up to respond. You need the culture,
and you need leaders who expect that. Then people can do amazing things,” Blank
says.
Chainguard: Outdated Containers Accumulate Vulnerabilities

EOL software is software that is no longer supported by the creator of the
application, either because it is an older version of the software that is no
longer maintained, or because the entities that maintained the software are no
longer around at all. In either case, vulnerabilities can still be found in
these applications, and since they are no longer patched, they soon become a
focus for actors with malicious intent. “And the problem becomes aggravated when
using container images,” Dunlap writes. “Using a container often means adding
additional components from underlying ‘base images,’ which can easily lead to
images with hundreds of components, each a part of the attack surface.” The
problem only grows worse over time for users, as without regular updates,
applications get harder and harder to update to the latest version over time.
Looking at software projects listed on endoflife.date, Dunlap found that the
longer a project has been EOL, the more vulnerabilities that image will collect.
This inspection included images for Traefik, F5’s NGINX, Rust, and Python.
Cisco: Security teams are ‘overconfident’ about handling next-gen threats

Part of the problem that most companies are facing, according to Cisco, is the
complicated nature of their security stacks. More than two-thirds of respondents
said that their company had more than 10 separate offerings in their security
stack, and a quarter said they had 30 or more. “This reflects the way in which
the industry has evolved over the years,” the report read. “As new threats
emerged, new solutions were developed and deployed to counter them, either by
existing vendors or new ones.” Frank Dickson, group vice president for IDC’s
security and trust research practice, said that the concern about complicated
tool stacks is far from a new one. “We’ve been having that debate in security
for ten years,” he said. Efforts to centralize security systems have been around
for just as long, he said, but for too long, the offerings peddled as
“platforms” weren’t really anything of the sort — more bundles of interrelated
products than true foundations for all-around security. That’s finally beginning
to change, however, Dickson said.
Saga Pattern in Microservices Architecture
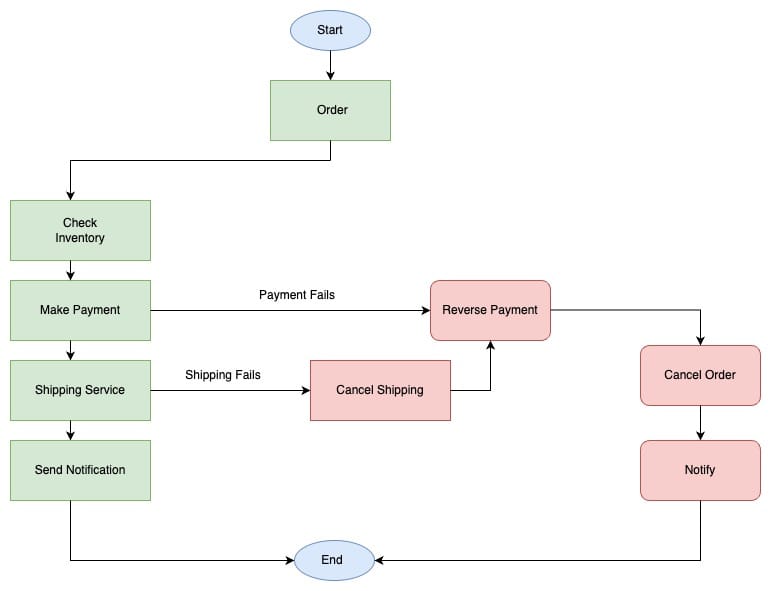
In a typical microservice-based architecture, where a single business use case
spans multiple microservices, each service has its own local datastore and
localized transaction. When it comes to multiple transactions, and the number
of microservices is vast, there comes the requirement to handle the
transaction spanning various services. ... The Saga Pattern is an
architectural pattern for implementing a sequence of local transactions that
helps maintain data consistency across different microservices. The local
transaction updates its database and triggers the next transaction by
publishing a message or event. If a local transaction fails, the saga executes
a series of compensating transactions to roll back the changes made by the
previous transactions. This ensures that the system remains consistent even
when transactions fail. ... The Saga Pattern can be implemented in two
different ways. Choreography: In this pattern, the individual microservices
consume the events, perform the activity, and pass the event to the next
service. ... Orchestration: In this pattern, all the microservices are linked
to the centralized coordinator that orchestrates the services in a predefined
order, thus completing the application flow.
Cisco warns of password-spraying attacks targeting VPN services

Security researcher Aaron Martin told BleepingComputer that the activity
observed by Cisco is likely from an undocumented malware botnet he named
‘Brutus.’ The connection is based on the particular targeting scope and attack
patterns. Martin has published a report on the Brutus botnet describing the
unusual attack methods that he and analyst Chris Grube observed since March
15. The report notes that the botnet currently relies on 20,000 IP addresses
worldwide, spanning various infrastructures from cloud services to residential
IPs. The attacks that Martin observed initially targeted SSLVPN appliances
from Fortinet, Palo Alto, SonicWall, and Cisco but have now expanded to also
include web apps that use Active Directory for authentication. Brutus rotates
its IPs every six attempts to evade detection and blocking, while it uses very
specific non-disclosed usernames that are not available in public data dumps.
This aspect of the attacks raises concerns about how these usernames were
obtained and might indicate an undisclosed breach or exploitation of a
zero-day vulnerability.
Understanding Polyglot Persistence: A Necessity for Modern Software Engineers and Architects
Unlock the Power of Polyglot Persistence with ‘Polyglot Persistence
Unleashed.’ This comprehensive guide embarks you on a transformative journey,
illustrating the integration of MongoDB, Cassandra, Neo4J, Redis, and
Couchbase within Enterprise Java Architecture. It delves deep into NoSQL
databases, Jakarta EE, and Microprofile, empowering you with the prowess to
architect and implement sophisticated data storage solutions for robust and
scalable Java applications. From in-depth exploration to practical examples,
optimization strategies, and pioneering insights, this book is your ultimate
guide to revolutionizing data management in your Java applications. ... The
Jakarta Data specification is a beacon of innovation for Java developers. It
offers a potent API that effortlessly bridges the diverse worlds of relational
and NoSQL databases. It fosters seamless integration of data access and
manipulation, adhering to a domain-centric architecture that simplifies
persistence complexities.
What Is AI TRiSM, and Why Is it Time to Care?

The goal of AI TRiSM is to place the necessary trust, risk and security
guardrails around AI systems so that enterprises can ensure that these systems
are accurate, secure and compliant. This can be a daunting undertaking, for
while there are many years of governance experience and best practices for
traditional applications and structured system of records data, there are few
established best practices when it comes to managing and analyzing AI
structured and unstructured data, and their applications, algorithms and
machine learning. How, for instance, do you vet all of the incoming volumes of
data from research papers all over the world that your AI might be analyzing
in an effort to develop a new drug? Or how can you ensure that you are
screening databases for the best job candidates if you are only using
your company’s past hiring history as your reference? ... In contrast, AI
systems have few established maintenance practices. When AI is first deployed,
it’s checked against what subject matter experts in the field would conclude,
and it must agree with what these experts conclude 95% of the time. Over time,
business, environmental, political and market conditions change.
Graph Databases: Benefits and Best Practices

The problems that can develop when working with graph databases include using
inaccurate or inconsistent data and learning to write efficient queries.
Accurate results rely on accurate and consistent information. If the data
going in isn’t reliable, the results coming out cannot be considered
trustworthy. This data query issue can also be a problem if the stored data
uses non-generic terms while the query uses generic terminology. Additionally,
the query must be designed to meet the system’s requirements. Inaccurate data
is based on information that is simply wrong. Blatant errors have been
included. Inaccurate data may include a wrong address, a wrong gender, or any
number of other errors. Inconsistent data, on the other hand, describes a
situation with multiple tables in a database working with the same data, but
receiving it from different inputs with slightly different versions
(misspellings, abbreviations, etc.). Inconsistencies are often compounded by
data redundancy. Graph queries interrogate the graph database, and these
queries need to be accurate, precise, and designed to fit the database model.
The queries should also be as simple as possible.
Quote for the day:
“Accomplishments will prove to be a
journey, not a destination.” -- Dwight D. Eisenhower
No comments:
Post a Comment