NCA’s Plaggemier on Finding a Path to Data Privacy Compliance
.jpg?width=850&auto=webp&quality=95&format=jpg&disable=upscale)
On the international stage, companies are becoming more aware of the more active
and robust policies they may face and the penalties they can carry. That has led
to some patterns, Plaggemier says, developing around what is reasonable for
companies to enact in relation to their sector and industry. “Do you have
security or privacy tools or practices in place that are in line with your
competitors?” she asks. While such an approach might be considered reasonable at
first, competitors might be way ahead with much more mature programs, Plaggemier
says, possibly making copying rivals no longer a reasonable approach and
compelling companies to find other ways to achieve compliance. Data privacy
regulations continue to gain momentum, and she believes it will be interesting
to see what further kind of enforcement actions develop and how the courts in
California, for example, manage. As CCPA and other state-level regulations
continue into their sophomore eras, Plaggemier says at least a few more states
seem likely to get on the bandwagon of data privacy regulation. Meanwhile, there
is also some growing concern about how AI may play a role in potential abuses of
data in the future.
What Is Enterprise Architecture? (And Why Should You Care About It)
Ideally, Enterprise Architecture supplies the context and insight to guide
Solution Architecture. To address broad considerations, and align diverse
stakeholder viewpoints, Enterprise Architecture often needs to be broader, less
specific, and often less technical than Solution Architecture. ... Done well,
Enterprise Architecture should provide long-term guidance on how different
technology components support overall business objectives. It should not
prescribe how technology is, or should be, implemented, but rather provide
guardrails that help inform design decisions and prioritization. Additionally,
most organizations have several technology components that support business
operations; Salesforce is usually just one. Understanding how the various
technology components work together will enable you to be a well-informed
contributing member of a larger team. EA can help to provide valuable context
about how Salesforce interacts with other systems and might spark ideas on how
Salesforce specifically can be better utilized to support an organization.
AnyDesk says hackers breached its production servers, reset passwords

In a statement shared with BleepingComputer late Friday afternoon, AnyDesk says
they first learned of the attack after detecting indications of an incident on
their product servers. After conducting a security audit, they determined their
systems were compromised and activated a response plan with the help of
cybersecurity firm CrowdStrike. AnyDesk did not share details on whether data
was stolen during the attack. However, BleepingComputer has learned that the
threat actors stole source code and code signing certificates. The company also
confirmed that the attack did not involve ransomware but didn't share too much
information about the attack other than saying their servers were breached, with
the advisory mainly focusing on how they responded to the attack. As part of
their response, AnyDesk says they have revoked security-related certificates and
remediated or replaced systems as necessary. They also reassured customers that
AnyDesk was safe to use and that there was no evidence of end-user devices being
affected by the incident. "We can confirm that the situation is under control
and it is safe to use AnyDesk.
The Ultimate 7-Step CEO Guide to Visionary Leadership
Unlike strategic objectives, which are rationally derived, visions are
values-laden. They give meaning through an ideological goal. Since they are
about what should be, they are, by definition, an expression of values and
corporate identity. Thus, effective CEOs keep the vision malleable in relation
to the business landscape but never change the values underneath. Not only that,
but their personal values align with the organization and its vision — one
reason for doing a values assessment in CEO succession. ... Some of the most
catastrophic events in history have been the result of a psychopath's vision.
Visions can be powerful, influential and morally corrupt — all at the same time.
Conversely, real leaders create a vision that benefits the entire ecosystem,
where the rising tide lifts all boats and makes the world a better place. Robert
House, from the University of Pennsylvania, defined a greater good vision as "an
unconscious motive to use social influence, or to satisfy the power need, in
socially desirable ways, for the betterment of the collective rather than for
personal self-interest." This is using the will to power for the betterment of
humanity, to shape the future, rather than as a source of ruthless evildoing.
AI Revolutionizes Voice Interaction: The Dawn Of A New Era In Technology

So what can we do to make sure we’re ready for this universal shift to
voice-controlled tech and having natural language conversations with machines?
Dengel suggests the answer lies in meeting the challenge head-on. This means
drawing together teams made of technologists, engineers, designers,
communications experts and business leaders. Their core focus is to identify
opportunities and potential risks to the business, allowing them to be managed
proactively rather than reactively. “That’s always the first step,” he says,
“because you start defining what’s possible, but you’re doing it in the context
of what’s realistic as well because you’ve got your tech folks involved as well
… ” It’s a “workshop” approach pioneered by Apple and adopted by various tech
giants that have found themselves at the forefront of an emerging wave of
transformation. But it’s equally applicable to just about any forward-looking
business or organization that doesn’t want to be caught off-guard. Dengel says
that addressing a group of interns recently, he told them, “I wish I were in
your shoes – the next five years is gonna be more innovation than there’s been
in the last five or maybe the last 20 years
Level up: Gamify Your Software Security

Gamification has been a great way to increase skills across the industry, and
this has become particularly important as adversaries become more
sophisticated and robust security becomes a critical piece to business
continuity. ... We all love our extrinsic motivators, whether it’s stars or
our green squares of activity on GitHub or even our badges and stickers in
forums and groups. So why not create a reward system for security too? This
makes it possible for developers to earn points, badges or status for
successfully integrating security measures into their code, recognizing their
achievements. ... Just as support engineers are often rewarded for the speed
and volume of tickets they close, similar ideas can be used to advance
security practices and hygiene in your organization. Use leaderboards to
encourage a healthy competitive spirit and recognize individuals or teams for
exceptional security contributions. ... This is in addition to the badges and
other rewards mentioned above. I’ve seen recognition programs for other
strategic initiatives in organizations, such as “Top Blogger” or “Top Speaker”
and even special hoodies or swag awarded to those who achieve the title,
giving it exclusivity and prestige.
802.11x: Wi-Fi standards and speeds explained

The big news in wireless is the expected ratification of Wi-Fi 7 (802.11be) by
the IEEE standards body early this year. Some vendors are already shipping
pre-standard Wi-Fi 7 gear, and the Wi-Fi Alliance announced in January that it
has begun certifying Wi-Fi 7 products. While the adoption of Wi-Fi 7 is
expected to have the most impact on the wireless market, the IEEE has been
busy working on other wireless standards as well. In 2023 alone, the group
published 802.11bb, a standard for communication via light waves; 802.11az,
which significantly improves location accuracy; and 802.11bd for
vehicle-to-vehicle wireless communication. Looking ahead, IEEE working groups
are tackling new technology areas, such as enhanced data privacy (802.11bi),
WLAN sensing (802.11bf), and randomized and changing MAC addresses (802.11bh).
In addition, the IEEE has established special-interest groups to investigate
the use of ambient energy harvested from the environment, such as heat, to
power IoT devices. There’s a study group looking at standards for
high-throughput, low-latency applications such as augmented reality/virtual
reality. Another group is developing new algorithms to support AI/ML
applications.
What is AI networking? Use cases, benefits and challenges

AI networking can optimize IT service management (ITSM) by handling the most
basic level 1 and level 2 support issues (like password resets or hardware
glitches). Leveraging NLP, chatbots and virtual agents can field the most
common and simple service desk inquiries and help users troubleshoot. AI can
also identify higher-level issues that go beyond step-by-step instructions and
pass them along for human support. AI networking can also help reduce trouble
ticket false-positives by approving or rejecting tickets before they are acted
on by the IT help desk. This can reduce the probability that human workers
will chase tickets that either weren’t real problems in the first place, were
mistakenly submitted or duplicated or were already resolved. ... AI can
analyze large amounts of network data and traffic and perform predictive
network maintenance. Algorithms can identify patterns, anomalies and trends to
anticipate potential issues before they degrade performance or cause
unexpected network outages. IT teams can then act on these to prevent — or at
least minimize — disruption. AI networking systems can also identify
bottlenecks, latency issues and congestion areas.
Low-Power Wi-Fi Extends Signals Up to 3 Kilometers
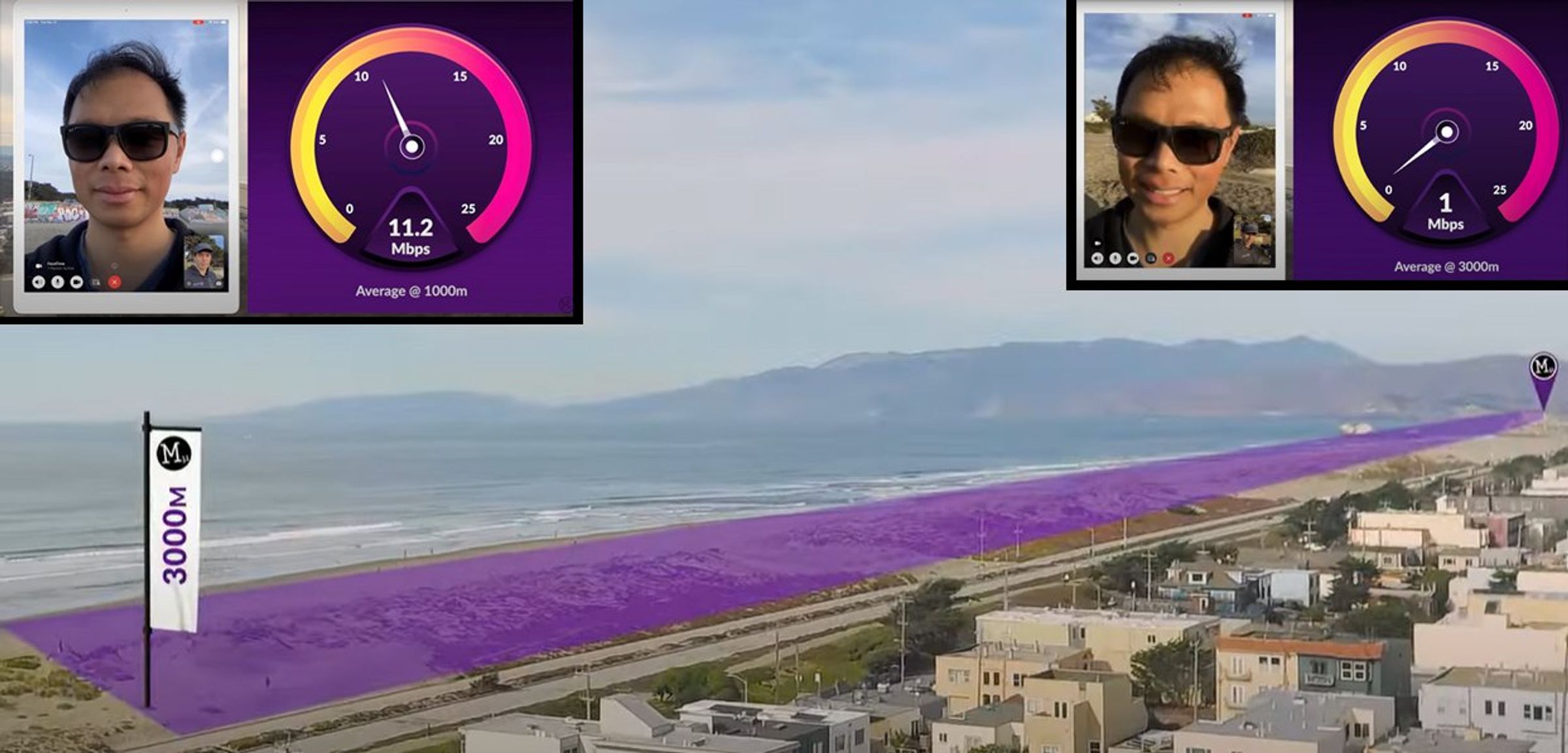
Morse Micro has developed a system-on-chip (SoC) design that uses a wireless
protocol called Wi-Fi HaLow, based on the IEEE 802.11ah standard. The protocol
significantly boosts range by using lower-frequency radio signals that
propagate further than conventional Wi-Fi frequencies. It is also low power,
and is geared toward providing connectivity for Internet of Things (IoT)
applications. To demonstrate the technology’s potential, Morse Micro recently
conducted a test on the seafront in San Francisco’s Ocean Beach neighborhood.
They showed that two tablets connected over a HaLow network could communicate
at distances of up to 3 km while maintaining speeds around 1 megabit per
second—enough to support a slightly grainy video call. ... “It is pretty
unprecedented range,” says Prakash Guda, vice president of marketing and
product management at Morse Micro. “And it’s not just the ability to send
pings but actual megabits of data.” The HaLow protocol works in much the same
way as conventional Wi-Fi, says Guda, apart from the fact that it operates in
the 900-megahertz frequency band rather than the 2.4-gigahertz band.
How to Make the Most of In-House Software Development
Maintaining an in-house software development team can be tough. You must hire
skilled developers – which is no easy feat in today’s economy, where talented
programmers remain in short supply – and then manage them on an ongoing basis.
You must also ensure that your development team is nimble enough to respond to
changing business needs and that it can adapt as your technology stack
evolves. Given these challenges, it’s no surprise that most organizations now
outsource application development instead of relying on in-house teams. But
I’m here to tell you that just because in-house development can be hard
doesn’t mean that outsourcing is always the best approach. On the contrary, IT
organizations that choose to invest in in-house development for some or all
the work can realize lower overall costs and a competitive advantage by
creating domain-specific expertise. Keeping development in-house can help
organizations address unique security requirements and maintain full control
over the development lifecycle and roadmaps. For businesses with specialized
technology, security and operational needs, in-house development is often the
best strategy.
Quote for the day:
“The first step toward success is
taken when you refuse to be a captive of the environment in which you first
find yourself.” -- Mark Caine
No comments:
Post a Comment