How is AI benefiting industries throughout Southeast Asia?
 AI in agriculture is mainly used for precision farming, livestock monitoring, drone analytics and agriculture robots. Precision farming was the most widely used application in 2018, taking up about 35.6% of the global total. However, agriculture robots are expected to have a bigger share in the future. Speaking at a recent seminar titled “Connecting Manufacturing Industry with AI Technology”, Dr Siridej Boonsaeng, Dean of the College of Advanced Manufacturing Innovation, King Mongkut's Institute of Technology Ladkrabang, said that AI is presenting the agricultural sector in Thailand with great opportunities. "Self-driving farm vehicles and the process of sorting and grading agricultural products which involve complicated factors of random shape and variation are suitable tasks for AI to replace human when required," he said. During last year’s Grow Asia Forum, Vietnam’s Deputy Prime Minister Trịnh Đình Dũng called for the private sector to get more involved with cutting edge technologies in the 4.0 revolution in a bid to transform the agriculture industry of Southeast Asian countries.
AI in agriculture is mainly used for precision farming, livestock monitoring, drone analytics and agriculture robots. Precision farming was the most widely used application in 2018, taking up about 35.6% of the global total. However, agriculture robots are expected to have a bigger share in the future. Speaking at a recent seminar titled “Connecting Manufacturing Industry with AI Technology”, Dr Siridej Boonsaeng, Dean of the College of Advanced Manufacturing Innovation, King Mongkut's Institute of Technology Ladkrabang, said that AI is presenting the agricultural sector in Thailand with great opportunities. "Self-driving farm vehicles and the process of sorting and grading agricultural products which involve complicated factors of random shape and variation are suitable tasks for AI to replace human when required," he said. During last year’s Grow Asia Forum, Vietnam’s Deputy Prime Minister Trịnh Đình Dũng called for the private sector to get more involved with cutting edge technologies in the 4.0 revolution in a bid to transform the agriculture industry of Southeast Asian countries.Lack of Secure Coding Called a National Security Threat
The lack of secure coding is a pervasive and serious threat to national security, according to a new paper from the Institute for Critical Infrastructure Technology, a cybersecurity think tank. Rob Roy, an ICIT fellow who was co-author of the report, suggests in an interview with Information Security Media Group that an app standards body could play an important role in improving app security. "If there were some objective standards put in place that all software would have to abide by, then we could start to make progress," Roy says. "It may just be that there needs to be an objective standard ... and a legislative mandate that requires a certain level of assurance to provide an assured product." The "call to action" report, "Software Security Is National Security: Why the U.S. Must Replace Irresponsible Practices with a Culture of Institutionalized Security," discusses systemic issues with the software development landscape and what needs to be done to rectify the problem of negligent coding. But solving the problem won't be easy, given the problems of speed-to-market pressures and the sheer number of IoT devices being produced, the report notes.Telangana launches draft Blockchain Policy
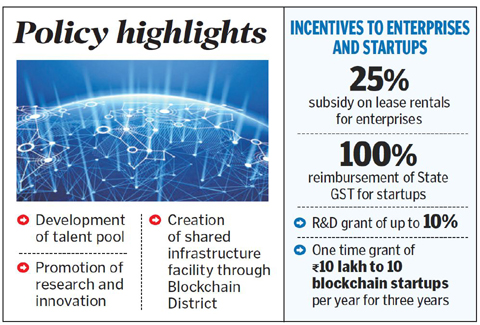
According to the draft framework, the Blockchain District will house all major blockchain technology companies; will have a huge incubator and a world-class facility for promoting research, innovation and industry collaboration. This one-of-its-kind initiative aims to put all blockchain companies based out of Hyderabad at a strategically advantageous position globally. The major highlights of the draft policy include the development of talent pool by collaborating with industries; creation of shared infrastructure facilities that can be used by startups, industry, academia and communities; promotion of research and innovation and enable collaboration and focus on community building. Other than these, the policy also looks at providing incentives and subsidies to enterprises, startups and other entities. While for enterprises, 25 per cent subsidy on lease rentals and 50 per cent subsidy on exhibition rentals will be provided, startups will get 100 per cent reimbursement of State GST, R&D grant of up to 10 per cent, one time grant of Rs 10 lakh to 10 blockchain startups per year for three years and patent filing assistance.

China's cybersecurity move is designed to both echo and address the U.S. sanctions against Huawei, as well as the country's leading surveillance equipment makers, including HikVision and Dahua. Under the new terms of reference, organizations within the country including network operators, IT services providers and even financial services companies, would need to conduct "comprehensive analysis and evaluation of risks brought about by national security." Nick Marro, a Hong Kong-based analyst with The Economist Intelligence Unit, told SCMP that "the regulatory opacity means that officials have quite a lot of flexibility in how they want to implement this - meaning it could be applied to U.S. firms in a way that embodies ‘qualitative measures’ as part of China’s trade war response." The goal, claims the Administration in its consultation document, is to "promote the application of advanced technologies, enhancing fairness and transparency, and protecting intellectual property rights." The Central Network Security and Informatization Committee "will take the national lead."
 "What we notice are new fields to enter credit card data that did not exist on the left (untampered form)," Segura writes in a blog post. By itself, this may not be out of the ordinary since online merchants do use such forms - including iFrame - as part of their checkout pages." Essentially, the iFrame jumps ahead in line. Although all PHP pages within the e-commerce site were infected, Segura says that the iFrame would only be triggered "if the current URL in the address bar is the shopping cart checkout page (onestepcheckout)." Apparently to help the malicious code avoid detection, "some extra checks (screen dimensions and presence of a web debugger) are also performed before continuing." The JavaScript that draws the iFrame comes from a domain, thatispersonal[.]com, which is hosted in Russia, Segura writes. Another script is used to process and validate the data. Once the victim enters their card details, the "data is sent via a POST request to the same malicious domain in a custom-encoded format." Finally, after that occurs, the user does get directed to the proper PSP, where they can pay.
"What we notice are new fields to enter credit card data that did not exist on the left (untampered form)," Segura writes in a blog post. By itself, this may not be out of the ordinary since online merchants do use such forms - including iFrame - as part of their checkout pages." Essentially, the iFrame jumps ahead in line. Although all PHP pages within the e-commerce site were infected, Segura says that the iFrame would only be triggered "if the current URL in the address bar is the shopping cart checkout page (onestepcheckout)." Apparently to help the malicious code avoid detection, "some extra checks (screen dimensions and presence of a web debugger) are also performed before continuing." The JavaScript that draws the iFrame comes from a domain, thatispersonal[.]com, which is hosted in Russia, Segura writes. Another script is used to process and validate the data. Once the victim enters their card details, the "data is sent via a POST request to the same malicious domain in a custom-encoded format." Finally, after that occurs, the user does get directed to the proper PSP, where they can pay.Why Blockchain-based Governance Requires In-Person Identity Verification
Any system of governance is vulnerable to this, so designing one that is “collusion-safe” is critical. Easier said than done because there is another component to the game theoretical design of “collusion-safe” design. It relates to identity. That second part is “identity-free.” If everyone in the system is anonymous, that makes collusion much, much more difficult. Imagine how difficult it would be for OPEC to exist if no one knew who the producers of oil were. Identity-free systems, however, bring up another issue. They are vulnerable to manipulation by mechanisms in a number of ways such as as bribing. You can read through the whole post, but the net of it is that in Vitalik’s mind, it is just not realistic to have a system that is both collusion-safe AND identity-free. It won’t work. Since compromising on collusion-safety is a non-starter, identity must be a key fixture. Furthermore, Vitalik suggests that the only realistic solution for identity is, ironically, in-person verification. At the end of the day, you need to show up and prove you are who you say you are.Deep learning explained

While you could write deep learning programs from first principles, it’s far more efficient to use deep learning frameworks, especially given that they have been optimized for use with GPUs and other accelerators. The pre-eminent framework is TensorFlow, which originated at Google. The favored high-level API for TensorFlow is Keras, which can also be used with other back-end frameworks. PyTorch, from Facebook and others, is a strong alternative to TensorFlow, and has the distinction of supporting dynamic neural networks, in which the topology of the network can change from epoch to epoch. Fastai is a high-level third-party API that uses PyTorch as a back-end. MXNet, from Amazon and others, is another strong alternative to TensorFlow, with a claim to better scalability. Gluon is the preferred high-level imperative API for MXNet. Chainer, from IBM, Intel, and others, was in some ways the inspiration for PyTorch, given that it defines the neural network by run and supports dynamic neural networks.
AI and machine learning driving skills revolution in business intelligence

An analyst’s role has become elevated over time, delivering a much more integral business impact. The research found a marked rise in a need for business skills (up 76% in the last five years versus 2009-2014), problem-solving (112%), and verbal communications skills (19%). Meanwhile, the need for Microsoft Excel (-49%), along with quantitative (-69%) and data analysis (-16%) skills, have all fallen considerably. Interpreting the results, Sir Cary Cooper, professor of organisational psychology at Alliance Manchester Business School, said: “In the future, the business analyst will be a different person. With AI and machine learning picking up mundane number-crunching work, the role now requires more innovative and original thinking. “This poses a challenge for employers in making sure they have people with the right skills in their workforce. As new technology comes into play, employers will need to re-evaluate the skills of their employees and develop training and recruitment practices that can make the most of the opportunities available.
Why office spaces should include Wi‑Fi‑enabled buses

If enough businesses were to offer such services, the environmental benefit could be tremendous. Cars generally emit around 0.7 pounds of carbon dioxide per mile; in heavy traffic, that can go up to two pounds. With 50 seats, the bus could prevent up to 100 pounds of carbon dioxide emissions for every mile of its route. Now imagine that such services would utilize the electric-battery buses that are slowly beginning to roll out on the roads. One study has found they’re 2.5 times cleaner than diesel buses on average. And in areas where hydro, wind, and solar account for a great deal of electricity, like the West Coast, the fuel powering these buses could be largely free of emissions. Of course, some employees might regard this as simply one more benefit — like the provision of free food and snacks on-site — aimed at tethering people more closely to their offices and promulgating an always-on culture. And that danger certainly exists. But the power of Wi-Fi-enabled buses lies in the option that it offers to employees. It’s a way to spend part of a standard workday, not extra hours in addition to one.
How Security Vendors Can Address the Cybersecurity Talent Shortage
While most efforts to address the talent shortage are centered on expanding technical skills to fill cybersecurity jobs, we need to be aware that the cybersecurity skills gap goes far beyond the job market for cybersecurity professionals. One of the biggest cyber-risks in today's workplace is a general lack of awareness of even the most basic attacks, such as phishing emails and other social engineering techniques. And that is due to a failure in understanding that cybersecurity is everyone's job, and organizations need training and education programs that address many different audiences. What cybersecurity vendors are usually quite good at is creating training programs to equip customers and partners with the knowledge and skills required to operate their own products. This is certainly critical as cybersecurity solutions become more sophisticated. ... Formal programs are a necessary element to filling the skills gap, but a comprehensive training and education strategy must include strategic partnerships within government, academia, and NGOs.Quote for the day:
"Real leadership is being the person others will gladly and confidently follow." -- John C. Maxwell
No comments:
Post a Comment