Quote for the day:
“Become the kind of leader that people would follow voluntarily, even if you had no title or position.” -- Brian Tracy
Is vibe coding ruining a generation of engineers?
 In the era of AI, the traditional journey to coding expertise that has long supported senior developers may be at risk. Easy access to large language models (LLMs) enables junior coders to quickly identify issues in code. While this speeds up software development, it can distance developers from their own work, delaying the growth of core problem-solving skills. As a result, they may avoid the focused, sometimes uncomfortable hours required to build expertise and progress on the path to becoming successful senior developers. ... The increasing availability of these tools from Anthropic, Microsoft and others may reduce opportunities for coders to refine and deepen their skills. Rather than “banging their heads against the wall” to debug a few lines or select a library to unlock new features, junior developers may simply turn to AI for an assist. This means senior coders with problem-solving skills honed over decades may become an endangered species. ... While concerns about AI diminishing human developer skills are valid, businesses shouldn’t dismiss AI-supported coding. They just need to think carefully about when and how to deploy AI tools in development. These tools can be more than productivity boosters; they can act as interactive mentors, guiding coders in real time with explanations, alternatives and best practices.
In the era of AI, the traditional journey to coding expertise that has long supported senior developers may be at risk. Easy access to large language models (LLMs) enables junior coders to quickly identify issues in code. While this speeds up software development, it can distance developers from their own work, delaying the growth of core problem-solving skills. As a result, they may avoid the focused, sometimes uncomfortable hours required to build expertise and progress on the path to becoming successful senior developers. ... The increasing availability of these tools from Anthropic, Microsoft and others may reduce opportunities for coders to refine and deepen their skills. Rather than “banging their heads against the wall” to debug a few lines or select a library to unlock new features, junior developers may simply turn to AI for an assist. This means senior coders with problem-solving skills honed over decades may become an endangered species. ... While concerns about AI diminishing human developer skills are valid, businesses shouldn’t dismiss AI-supported coding. They just need to think carefully about when and how to deploy AI tools in development. These tools can be more than productivity boosters; they can act as interactive mentors, guiding coders in real time with explanations, alternatives and best practices.How Reassured Are You by Your Cloud Compliance?
 For organizations, the assurance of a secure cloud hinges on proficient NHI management. By implementing a strategic plan, companies can significantly bolster their defenses against unauthorized access and potential threats. Understanding and managing machine identities becomes a crucial pillar of cloud assurance strategies. ... With organizations strive to maintain their competitive edge, the strategic importance of NHIs in ensuring compliance and security cannot be overstated. By fostering a culture of security awareness and leveraging robust management platforms, businesses can confidently navigate the complex terrain of cloud compliance. ... Compliance is a formidable challenge. However, NHI management offers actionable solutions to these challenges. By auditing and tracking NHIs, organizations gain unparalleled visibility into access patterns and potential breaches, ensuring adherence to relevant regulatory frameworks across multiple sectors. Automation of audit trails and enforcement of policies can significantly reduce the burden on compliance teams, allowing companies to focus on strategic areas of business development. Additionally, adaptive NHI management systems can be scaled and updated to align with new compliance standards. This flexibility positions businesses to react quickly to regulatory changes without incurring significant downtime or resource allocation shifts.
For organizations, the assurance of a secure cloud hinges on proficient NHI management. By implementing a strategic plan, companies can significantly bolster their defenses against unauthorized access and potential threats. Understanding and managing machine identities becomes a crucial pillar of cloud assurance strategies. ... With organizations strive to maintain their competitive edge, the strategic importance of NHIs in ensuring compliance and security cannot be overstated. By fostering a culture of security awareness and leveraging robust management platforms, businesses can confidently navigate the complex terrain of cloud compliance. ... Compliance is a formidable challenge. However, NHI management offers actionable solutions to these challenges. By auditing and tracking NHIs, organizations gain unparalleled visibility into access patterns and potential breaches, ensuring adherence to relevant regulatory frameworks across multiple sectors. Automation of audit trails and enforcement of policies can significantly reduce the burden on compliance teams, allowing companies to focus on strategic areas of business development. Additionally, adaptive NHI management systems can be scaled and updated to align with new compliance standards. This flexibility positions businesses to react quickly to regulatory changes without incurring significant downtime or resource allocation shifts.AI Powered SOC: The Shift from Reactive to Resilient
 Current SOC operations are described as “buried — not just in alert volume, but in disconnected tools, fragmented telemetry, expanding cloud workloads, and siloed data.” This paints a picture of overwhelmed teams struggling to maintain control in an increasingly complex threat landscape. ... With AI Agents, automated response actions, such as containment and remediation, can be executed with human oversight for high-impact situations. AI can handle routine containment and remediation tasks, such as isolating a compromised host or blocking a malicious hash. After an action is taken, the AI can perform validation checks to ensure business operations are not negatively impacted, with automatic rollback triggers if necessary. ... This transition is not a flip of a switch; it is a strategic journey. The organizations that succeed will be those who invest in integrating AI with existing security ecosystems, upskill their talent to work with these new technologies, and ensure robust governance is in place. Embracing an AI-powered SOC is no longer optional but a strategic imperative. By building a partnership between human expertise and machine efficiency, organizations will transform their security operations from a vulnerable cost center into a resilient and agile business enabler. AI is not a silver bullet—but it’s a strategic lever. The SOC of the future won’t just detect threats; it will predict, prevent, and persist. Shifting to resilience means embracing AI not as a tool, but as a partner in defending digital trust.
Current SOC operations are described as “buried — not just in alert volume, but in disconnected tools, fragmented telemetry, expanding cloud workloads, and siloed data.” This paints a picture of overwhelmed teams struggling to maintain control in an increasingly complex threat landscape. ... With AI Agents, automated response actions, such as containment and remediation, can be executed with human oversight for high-impact situations. AI can handle routine containment and remediation tasks, such as isolating a compromised host or blocking a malicious hash. After an action is taken, the AI can perform validation checks to ensure business operations are not negatively impacted, with automatic rollback triggers if necessary. ... This transition is not a flip of a switch; it is a strategic journey. The organizations that succeed will be those who invest in integrating AI with existing security ecosystems, upskill their talent to work with these new technologies, and ensure robust governance is in place. Embracing an AI-powered SOC is no longer optional but a strategic imperative. By building a partnership between human expertise and machine efficiency, organizations will transform their security operations from a vulnerable cost center into a resilient and agile business enabler. AI is not a silver bullet—but it’s a strategic lever. The SOC of the future won’t just detect threats; it will predict, prevent, and persist. Shifting to resilience means embracing AI not as a tool, but as a partner in defending digital trust.Cybersecurity As A Strategy: The CIO’s Playbook for a Perma-Threat Landscape
 When cybersecurity is seen as a strategic function, it helps businesses stay strong. It protects intellectual property, makes sure that rules are followed, and builds the trust of customers, partners, and other stakeholders. It can also help businesses be more innovative by letting them look into new markets, use new technologies, and change how they do business with confidence. The main point of this playbook is simple: CIOs need to stop using reactive defense models and start seeing cybersecurity as a key part of their business strategy. In a world where threats are always present, the companies that do well will be the ones whose leaders see cyber resilience as important for brand reputation, business continuity, and staying ahead of the competition. ... In this situation, being reactive is not only dangerous, it’s also costly. The costs of a cyberattack go well beyond fixing the damage right away. Companies can be fined by the government, sued, lose money when their systems go down, and have to pay more for insurance. The reputational damage can be even more devastating: loss of customer trust, decreased investor confidence, and long-term brand erosion. According to studies in the field, the average cost of a data breach is now over a million dollars, and high-profile cases have cost hundreds of millions. ... CIOs need to stop thinking about “building walls and patching holes” and start thinking about how to find, stop, and neutralize threats before they can do any damage.
When cybersecurity is seen as a strategic function, it helps businesses stay strong. It protects intellectual property, makes sure that rules are followed, and builds the trust of customers, partners, and other stakeholders. It can also help businesses be more innovative by letting them look into new markets, use new technologies, and change how they do business with confidence. The main point of this playbook is simple: CIOs need to stop using reactive defense models and start seeing cybersecurity as a key part of their business strategy. In a world where threats are always present, the companies that do well will be the ones whose leaders see cyber resilience as important for brand reputation, business continuity, and staying ahead of the competition. ... In this situation, being reactive is not only dangerous, it’s also costly. The costs of a cyberattack go well beyond fixing the damage right away. Companies can be fined by the government, sued, lose money when their systems go down, and have to pay more for insurance. The reputational damage can be even more devastating: loss of customer trust, decreased investor confidence, and long-term brand erosion. According to studies in the field, the average cost of a data breach is now over a million dollars, and high-profile cases have cost hundreds of millions. ... CIOs need to stop thinking about “building walls and patching holes” and start thinking about how to find, stop, and neutralize threats before they can do any damage. What to look for in a data protection platform for hybrid clouds
 Data protection is a broad category that includes data security but also encompasses backup and disaster recovery, safe data storage, business continuity and resilience, and compliance with data privacy regulations. ... In the public cloud model, the hyperscalers (such as Amazon Web Services, Google Cloud, and Microsoft Azure) are responsible for protecting their own infrastructure, but the enterprise using them — you — is responsible for properly configuring and managing its own data in the cloud. One of the most common causes of cloud-based data breaches is a simple misconfiguration of an Amazon S3 storage bucket. Cloud security posture management (CSPM) tools can help identify misconfigurations, among other risks. ... Data protection can be performed with on-premises appliances or in the cloud. And organizations can manage their data protection functionality themselves or turn to a managed service. The trend lines are clear: Just as applications and data are moving to the cloud, data protection is moving to the cloud as well, due to the scalability, flexibility, and accessibility that the cloud provides. ... Because every enterprise is different and because hybrid clouds are both complex and varied in their handling of data, you need to get a clear grasp on your specific needs, capabilities, and resources before engaging prospective vendors and then choosing specific solutions for data protection.
Data protection is a broad category that includes data security but also encompasses backup and disaster recovery, safe data storage, business continuity and resilience, and compliance with data privacy regulations. ... In the public cloud model, the hyperscalers (such as Amazon Web Services, Google Cloud, and Microsoft Azure) are responsible for protecting their own infrastructure, but the enterprise using them — you — is responsible for properly configuring and managing its own data in the cloud. One of the most common causes of cloud-based data breaches is a simple misconfiguration of an Amazon S3 storage bucket. Cloud security posture management (CSPM) tools can help identify misconfigurations, among other risks. ... Data protection can be performed with on-premises appliances or in the cloud. And organizations can manage their data protection functionality themselves or turn to a managed service. The trend lines are clear: Just as applications and data are moving to the cloud, data protection is moving to the cloud as well, due to the scalability, flexibility, and accessibility that the cloud provides. ... Because every enterprise is different and because hybrid clouds are both complex and varied in their handling of data, you need to get a clear grasp on your specific needs, capabilities, and resources before engaging prospective vendors and then choosing specific solutions for data protection.Git Services Need Better Security. Here’s How End-to-End Encryption Could Help
 Most development teams rely on platforms like GitHub, GitLab, or Bitbucket to manage their projects and collaborate across teams. These services work well for version control and collaboration, but there’s a problem. System breaches have become common, and the data stored in repositories can be highly valuable to attackers. Think about what’s in your repositories. Source code, API keys, infrastructure configurations, and the complete history of your project’s development. If someone gains unauthorized access to your Git service provider’s systems, they can access all of that. Current solutions don’t effectively address this problem. Some open-source projects have attempted to add encryption to Git workflows, but they suffer from two major issues: weak security guarantees and poor performance. The overhead is so large that most teams won’t adopt them. ... End-to-end encryption for Git services would mean that even if your service provider’s systems are compromised, your code remains secure. The provider wouldn’t have the keys to decrypt your repositories. This level of security has become standard for messaging apps and cloud storage. It makes sense to apply the same principles to Git services, especially given the value of what’s stored there. For regulated industries, this could help meet compliance requirements. For any organization with valuable intellectual property, it adds an important layer of protection.
Most development teams rely on platforms like GitHub, GitLab, or Bitbucket to manage their projects and collaborate across teams. These services work well for version control and collaboration, but there’s a problem. System breaches have become common, and the data stored in repositories can be highly valuable to attackers. Think about what’s in your repositories. Source code, API keys, infrastructure configurations, and the complete history of your project’s development. If someone gains unauthorized access to your Git service provider’s systems, they can access all of that. Current solutions don’t effectively address this problem. Some open-source projects have attempted to add encryption to Git workflows, but they suffer from two major issues: weak security guarantees and poor performance. The overhead is so large that most teams won’t adopt them. ... End-to-end encryption for Git services would mean that even if your service provider’s systems are compromised, your code remains secure. The provider wouldn’t have the keys to decrypt your repositories. This level of security has become standard for messaging apps and cloud storage. It makes sense to apply the same principles to Git services, especially given the value of what’s stored there. For regulated industries, this could help meet compliance requirements. For any organization with valuable intellectual property, it adds an important layer of protection.Bringing authentication into the AI century
 Today’s customer journey flows much differently than before, spreading across devices, shaped by automation, and powered by artificial intelligence (AI) assistants. What worked five years or even one year ago might already be standing in the way of creating impactful experiences. ... Authentication flows that anticipate outdated behavior and patterns, like expecting static sessions and manual inputs, aren’t able to keep up with the new normal of digital commerce. Patterns that used to look suspicious, including ultra-fast clicks and cross-device shopping, might be totally legitimate. However, if legacy systems can’t tell the difference, the experience of real customers will suffer. They might get flagged as fraud and experience friction, ultimately ending in a negative experience and a lost sale. Furthermore, you must choose the right authentication method in accordance with specific fraud MOs to avoid letting fraud slip through the cracks. ... Leaders don’t need to choose between protecting their business and giving customers the smooth experience they expect. Modern authentication must be built on trust, timing, and intelligence, rather than interruptions. ... Authentication needs to be just as dynamic as today’s fraudsters. It’s not about adding more steps; it’s about smarter context, stronger signals, and systems that can keep up. When trust drives your flow, authentication works seamlessly in the background, keeping real customers loyal and real risks out.
Today’s customer journey flows much differently than before, spreading across devices, shaped by automation, and powered by artificial intelligence (AI) assistants. What worked five years or even one year ago might already be standing in the way of creating impactful experiences. ... Authentication flows that anticipate outdated behavior and patterns, like expecting static sessions and manual inputs, aren’t able to keep up with the new normal of digital commerce. Patterns that used to look suspicious, including ultra-fast clicks and cross-device shopping, might be totally legitimate. However, if legacy systems can’t tell the difference, the experience of real customers will suffer. They might get flagged as fraud and experience friction, ultimately ending in a negative experience and a lost sale. Furthermore, you must choose the right authentication method in accordance with specific fraud MOs to avoid letting fraud slip through the cracks. ... Leaders don’t need to choose between protecting their business and giving customers the smooth experience they expect. Modern authentication must be built on trust, timing, and intelligence, rather than interruptions. ... Authentication needs to be just as dynamic as today’s fraudsters. It’s not about adding more steps; it’s about smarter context, stronger signals, and systems that can keep up. When trust drives your flow, authentication works seamlessly in the background, keeping real customers loyal and real risks out.From Automation to Autonomy: Agentic AI set to transform India’s telecom sector
 KPMG’s report introduces the Agentic AI Stack for Indian Telcos, a six-layer model covering customer experience, network intelligence, orchestration, data integration, and governance, designed to guide operators from traditional networks toward intelligent, autonomous systems. Current adoption trends show that half of telecom companies have implemented their first GenAI use case, and business leaders are planning to invest USD 25 million in new tech talent and USD 24 million in customer experience initiatives over the next 12 months. Looking ahead, KPMG recommends that telecom operators scale AI pilots to enterprise-wide deployments with AI-ready infrastructure and skilled teams, while policymakers should create agile regulations and governance frameworks to enable safe and responsible AI innovation. Collaboration among startups, academia, and industry partners is critical to building an inclusive and intelligent telecom ecosystem. “Agentic AI is more than a technological advancement — it is a strategic paradigm shift that empowers telecom operators to move from reactive to autonomous systems,” said Akhilesh Tuteja, Partner & National Leader – Technology, Media and Telecommunications (TMT), KPMG in India. “This transformation will unlock new levels of operational efficiency, customer personalization, and revenue growth. India’s unparalleled scale, data richness, and innovation ecosystem uniquely position it to lead the global telecom AI revolution.”
KPMG’s report introduces the Agentic AI Stack for Indian Telcos, a six-layer model covering customer experience, network intelligence, orchestration, data integration, and governance, designed to guide operators from traditional networks toward intelligent, autonomous systems. Current adoption trends show that half of telecom companies have implemented their first GenAI use case, and business leaders are planning to invest USD 25 million in new tech talent and USD 24 million in customer experience initiatives over the next 12 months. Looking ahead, KPMG recommends that telecom operators scale AI pilots to enterprise-wide deployments with AI-ready infrastructure and skilled teams, while policymakers should create agile regulations and governance frameworks to enable safe and responsible AI innovation. Collaboration among startups, academia, and industry partners is critical to building an inclusive and intelligent telecom ecosystem. “Agentic AI is more than a technological advancement — it is a strategic paradigm shift that empowers telecom operators to move from reactive to autonomous systems,” said Akhilesh Tuteja, Partner & National Leader – Technology, Media and Telecommunications (TMT), KPMG in India. “This transformation will unlock new levels of operational efficiency, customer personalization, and revenue growth. India’s unparalleled scale, data richness, and innovation ecosystem uniquely position it to lead the global telecom AI revolution.”TRIAL: Charting the Path from SCREAM to AARAM – A Simplified Guide for Effective Enterprise Architecture
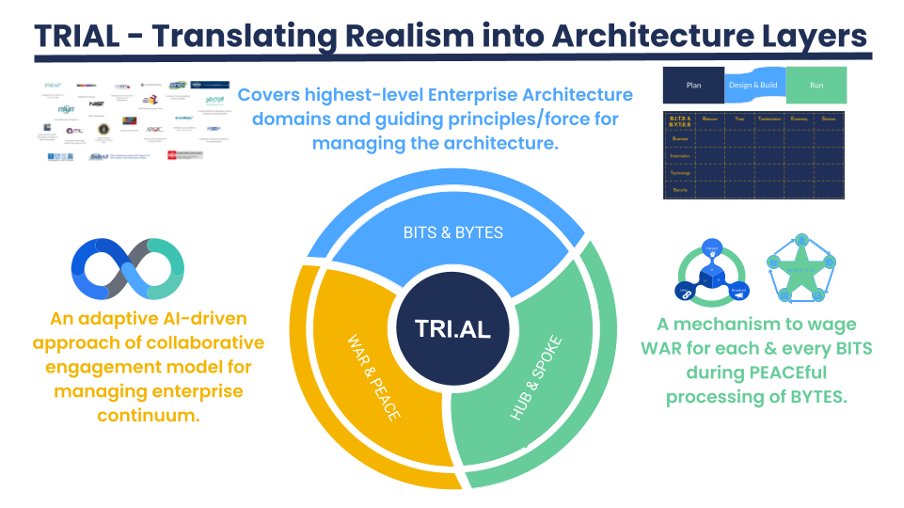 Despite billions invested annually in enterprise architecture (EA), organizations grapple with a persistent gap between theoretical frameworks and practical execution. In 2025, 94% of CIOs deem EA “absolutely critical” for embedding sustainability and driving digital resilience, yet 57% of architects report feeling underutilized in strategic initiatives. ... At its core, architecture is about effectively managing the lifecycle changes of architecture components and their relationships. TRIAL establishes an EA approach that resonates with architects and stakeholders by embracing these lifecycle stages as central motifs. This approach captures and builds a data and AI-driven architecture around its underlying evolving repository continuum, leveraging the same engagement model for collaborative execution aligned with organizational objectives. ... Enterprise architecture maturity traditionally requires skilled resources, extensive knowledge, and significant time investment. Organizations face resource scarcity while architects average only 18-24 months tenure, making adaptive architecture management nearly impossible. This challenge is exacerbated by broader technology trends, where 70-85% of enterprise AI projects fail due to poor data management, misalignment with business goals, and architectural oversights—rates double those of non-AI IT projects. TRIAL addresses this through progressive maturity states that build upon each other. Organizations advance through clearly defined maturity levels—from Balanced (foundation) through Yearly (planning),
Despite billions invested annually in enterprise architecture (EA), organizations grapple with a persistent gap between theoretical frameworks and practical execution. In 2025, 94% of CIOs deem EA “absolutely critical” for embedding sustainability and driving digital resilience, yet 57% of architects report feeling underutilized in strategic initiatives. ... At its core, architecture is about effectively managing the lifecycle changes of architecture components and their relationships. TRIAL establishes an EA approach that resonates with architects and stakeholders by embracing these lifecycle stages as central motifs. This approach captures and builds a data and AI-driven architecture around its underlying evolving repository continuum, leveraging the same engagement model for collaborative execution aligned with organizational objectives. ... Enterprise architecture maturity traditionally requires skilled resources, extensive knowledge, and significant time investment. Organizations face resource scarcity while architects average only 18-24 months tenure, making adaptive architecture management nearly impossible. This challenge is exacerbated by broader technology trends, where 70-85% of enterprise AI projects fail due to poor data management, misalignment with business goals, and architectural oversights—rates double those of non-AI IT projects. TRIAL addresses this through progressive maturity states that build upon each other. Organizations advance through clearly defined maturity levels—from Balanced (foundation) through Yearly (planning),
No comments:
Post a Comment