Cisco automation tools make it easier for network admins

Cisco has a new automation software portfolio that helps global service providers manage massive amounts of network data and better prepare for impending security threats. "We built out an entirely new portfolio of automation tools. It really centers on the fact that our customers have a whole set of challenges. They're currently spending on average somewhere between 3-4 times the amount to operate an infrastructure than they are just to purchase the infrastructure," said Jonathan Davidson, senior vice president and general manager of Cisco Service Provider Networking. In 2016, there were 17 billion devices and connections running on service provider networks and this is forecast to grow to 27 billion by 2021. To address this shift, the Cisco Crosswork Network Automation portfolio will assist industry adoption of complete lifecycle network automation and intent-based networking to help networks predict change and react in near real time.
Leveraging Security to Enable Your Business
The first step is to look into more modern technologies, such as a reverse proxy, which can overcome the cumbersome nature of multiple VPNs and ensure quick, seamless, and secure access from anywhere, on any device. With this approach, there is no need to repeatedly require MFA once a user has "passed the test" of proving who they are. Businesses can also leverage adaptive authentication technology, which automatically adjusts authentication requirements relative to the risk of the request. For example, an initial login may require MFA, but subsequent logins by the same user, from the same device, in the same day would not. If, however, the request suddenly comes from an unknown device, there could be something fishy going on. With adaptive authentication, the rules for an MFA requirement for specific risky login instances can be preset and automatically enforced.
AI for good: Can AI be trusted - and is it too late to ask?
The answer seems to point towards human input: in the words of AI researcher Professor Joanna Bryson, “if the underlying data reflects stereotypes, or if you train AI from human culture, you will find bias.” And if we’re not careful, we risk integrating that bias into the computer programs that are fast taking over the running of everything from hospitals to schools to prisons – programs that are supposed to eliminate those biases in the first place. Nigel Willson, global strategist at Microsoft, points out the importance of recognising how no technology is ever black and white. “The reality is that AI is like anything else – it can be very dangerous, or it can be amazing, based on how it’s used or misused,” he says. AI is only as as accurate as the information on which it is trained – meaning that we must be very careful with how we train it. Awareness of ‘unfair’ bias integrated into decades of data has led researchers to attempt the design of algorithms that counteract that bias when scraping the data: but this sparks the question of what constitutes ‘fairness’.
Telecom Opportunities: How to Monetize IoT
When League of Legends, one of the most popular online video games, went through the issue of lagging, their developers created their own internet to let players connect to the game. Riot Games created a network of routers, data centers and peer ISPs to create a network that placed latency before costs. Players from any part of the country would be directly connected to Riot’s access servers rather than routers on the regular ISP network. With 5G, Telcos can offer new levels of latency but there is more than just network connectivity that they can offer to gaming companies. One example Ericsson showed me during a recent visit to Kista, Sweden was an interface that allowed the gamer to manage their account from inside the game, for example they could top up their data allowance without having to exit the game.
“There is also growing use of managed security services to complement their on-site capability and provide secure file transfers and software updates, as well as continuous monitoring,” he said. However, he said that although there is a high level of awareness of the need for good cyber security in industrial operations, in many cases cyber security fundamentals are not yet in place. A recent Honeywell-sponsored survey by LNS Research of 130 decision makers from industrial companies revealed that only 37% were monitoring their plant systems for suspicious behaviour and 20% are not conducting regular risk assessments. “The survey also found that 53% said they had already experienced cyber security breach, but that is not surprising, given how young we are globally in cyber protection for critical infrastructure and industrial cyber security,” said Zindel.
Big Data Isn’t a Thing; Big Data is a State of Mind

Big Data is about exploiting the unique characteristics of data and analytics as digital assets to create new sources of economic value for the organization. Most assets exhibit a one-to-one transactional relationship. For example, the quantifiable value of a dollar as an asset is finite – it can only be used to buy one item or service at a time. Same with human assets, as a person can only do one job at a time. But measuring the value of data as an asset is not constrained by those transactional limitations. In fact, data is an unusual asset as it exhibits an Economic Multiplier Effect, whereby it never depletes or wears out and can be used simultaneously across multiple use cases at near zero margin cost. This makes data a powerful asset in which to invest. Understanding the economic characteristics of data and analytics as digital assets is the first step in monetizing your data via predictive, prescriptive and preventative analytics.
How long does it take to detect a cyber attack?
The study found that US companies took an average of 206 days to detect a data breach. This is a slight increase on the previous year (201 days). Ponemon suggests all organizations should aim to identify a breach within 100 days. The average cost of identifying a breach within this time was $5.99 million, but for breaches that took longer to identify, the average cost rose to $8.70 million. There is a similar correlation in terms of containing a breach. Breaches that took less than 30 days to contain had an average cost of $5.87 million, but this rose to $8.83 million for breaches that took longer to contain. The good news is that organizations have become significantly better at containing breaches, with the average time dropping from 70 days in 2016 to 55 days. The majority of breached organizations are notified by someone other than their own staff, according to Mandiant’s M-Trends 2017 report. It found that 53% of breaches were discovered by an external source.
Hackers are selling legitimate code-signing certificates to evade malware detection

Code-signing certificates are designed to give your desktop or mobile app a level of assurance by making apps look authentic. Whenever you open a code-signed app, it tells you who the developer is and provides a high level of integrity to the app that it hasn't been tampered with in some way. Most modern operating systems, including Macs, only run code-signed apps by default. But not only does code-signing have an affect on users who inadvertently install malware, code-signed apps are also harder to detect by network security appliances. The research said that hardware that uses deep packet inspection to scan for network traffic "become less effective when legitimate certificate traffic is initiated by a malicious implant." That's been picked up by some hackers, who are selling code-signing certificates for as little as $299. Extended validation certificates which are meant to go through a rigorous vetting process can be sold for $1,599.
Machine-learning promises to shake up large swathes of finance
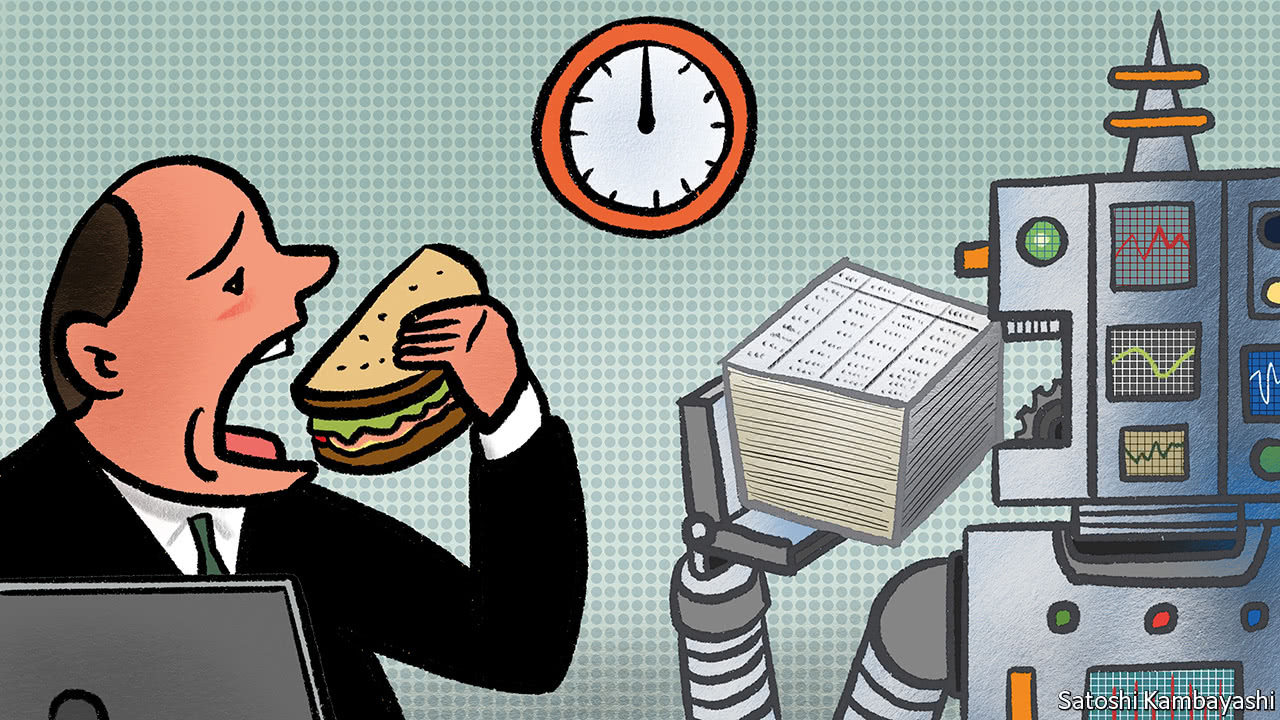
Natural-language processing, where AI-based systems are unleashed on text, is starting to have a big impact in document-heavy parts of finance. In June 2016 JPMorgan Chase deployed software that can sift through 12,000 commercial-loan contracts in seconds, compared with the 360,000 hours it used to take lawyers and loan officers to review the contracts. Machine-learning is also good at automating financial decisions, whether assessing creditworthiness or eligibility for an insurance policy. Zest Finance has been in the business of automated credit-scoring since its founding in 2009. Earlier this year it rolled out a machine-learning underwriting tool to help lenders make credit decisions, even for people with little conventional credit-scoring information. It sifts through vast amounts of data, such as people’s payment history or how they interact with a lender’s website.
The emerging link between employee well-being and cyber security services
This epidemic means big problems for employees and employers alike — and a significant opportunity for brokers who can provide solutions that protect employees’ financial well-being. When identity thieves take advantage of employees’ stolen personal information to obtain credit or loans, or commit various types of fraud, both employees and employers pay a steep price. ... In other words, the identity theft resolution process is not only stressful for employees, it has a significant impact on their productivity at work. The reason is because without the assistance of an identity theft resolution resource, employees have to do a lot of leg work, such as filing police reports, writing letters and making trips to financial institutions to report fraud.
Quote for the day:
"You never really learn much from hearing yourself speak." -- George Clooney

No comments:
Post a Comment