How blockchain will underpin the new trust economy

As a peer-to-peer network, combined with a distributed time-stamping servers, blockchain databases can be managed autonomously to exchange information between disparate parties. There's no need for an administrator. In effect, the blockchain users are the administrator. In the trust economy, an individual's or entity's "identity" confirms membership in a nation or community; ownership of assets; entitlement to benefits or services; and, more fundamentally, as evidence that the person or entity exists, according to Deloitte. Blockchain doesn't simply solve data access or sharing issues; it also solves a confidence problem. In the peer-to-peer trust economy, an individual user – not a third party – will determine what digital information is recorded in a blockchain and how that information will be used.
Cybersecurity concerns may stop consumers from purchasing a connected car

The desire to consider cybersecurity when purchasing a car was most prevalent with younger generations aged 25-34, with 62% stating they would conduct this research. On the opposite end of the spectrum, only 43% of consumers 55+ would look into the car’s cybersecurity protection. “It’s clear that cybersecurity will be a key factor for many consumers when they are purchasing their next vehicle,” said Daniel Thunberg, Global Head, Connected Transport, Irdeto. “It is important for automakers to make security a priority by implementing a multi-layered, defense in-depth strategy so their brand is not perceived by consumers as one that does not take security seriously. By implementing security at the beginning of the manufacturing process, OEMs and Tier 1 suppliers will not only stay one step ahead of hackers, but will show consumers that they are committed to their safety by implementing a proper security approach.”
What to expect with pervasive encryption on IBM mainframes

Data set encryption requires extended format files and encompasses most basic sequential files and all forms of Virtual Storage Access Method (VSAM) data sets. It does leave a couple curious holes by excluding partitioned data sets and tapes. Information Management System v14 allows data set encryption for a subset of data sets, while IMS v15 will have full support. Users can encrypt the Coupling Facility cache and list structures as well through CF Resource Manager policy. IBM's z/OS encrypts the data for protection both in flight and at rest in the CF. The z/OS's System Authorization Facility controls access to encryption keys and functions to very granular levels. This could lead to situations where someone may be authorized to read a data set but unable to decrypt it. This is the perfect setup for storage and database administrators.
Which of Your Employees Are Most Likely to Expose Your Company to a Cyberattack?

Basic human behavior is very hard to reprogram. Therefore, training should be augmented by constantly updating technology, which has now evolved to detect errant behavior. The advancement of technology has only just begun to solve what seemed to be intractable issues in security and governance, and these new capabilities such as predictive analytics and artificial intelligence are expected to better monitor and influence human behavior. By employing a modern breed of analytics that enables organizations to analyze documents for sensitive content, review user actions, and track the flow of data across the enterprise, cybersecurity stakeholders can now identify many common indicators of negligent or malicious activity
Top 10 Technology Trends Impacting Infrastructure & Operations for 2018
In 2018, IT will be increasingly tasked with supporting complex, distributed applications using new technologies that are spread across systems in multiple locations, including on-premises data centers, the public cloud and hosting providers. During the Gartner IT Infrastructure, Operations Management and Data Center Conference in Las Vegas, David Cappuccio, vice president and distinguished analyst at Gartner, said I&O leaders should focus on 10 key technologies and trends to support digital transformation. “These are not necessarily the top 10 technologies, or the hottest trends in IT, but rather the 10 trends we feel will have an impact on I&O teams over the next few years,” says Cappuccio. “Some are happening already, some are just beginning, but each will have an impact on how IT operates, plans, enhances internal skill sets, and supports the business.”
The OSI model explained: How to understand (and remember) the 7 layer network model
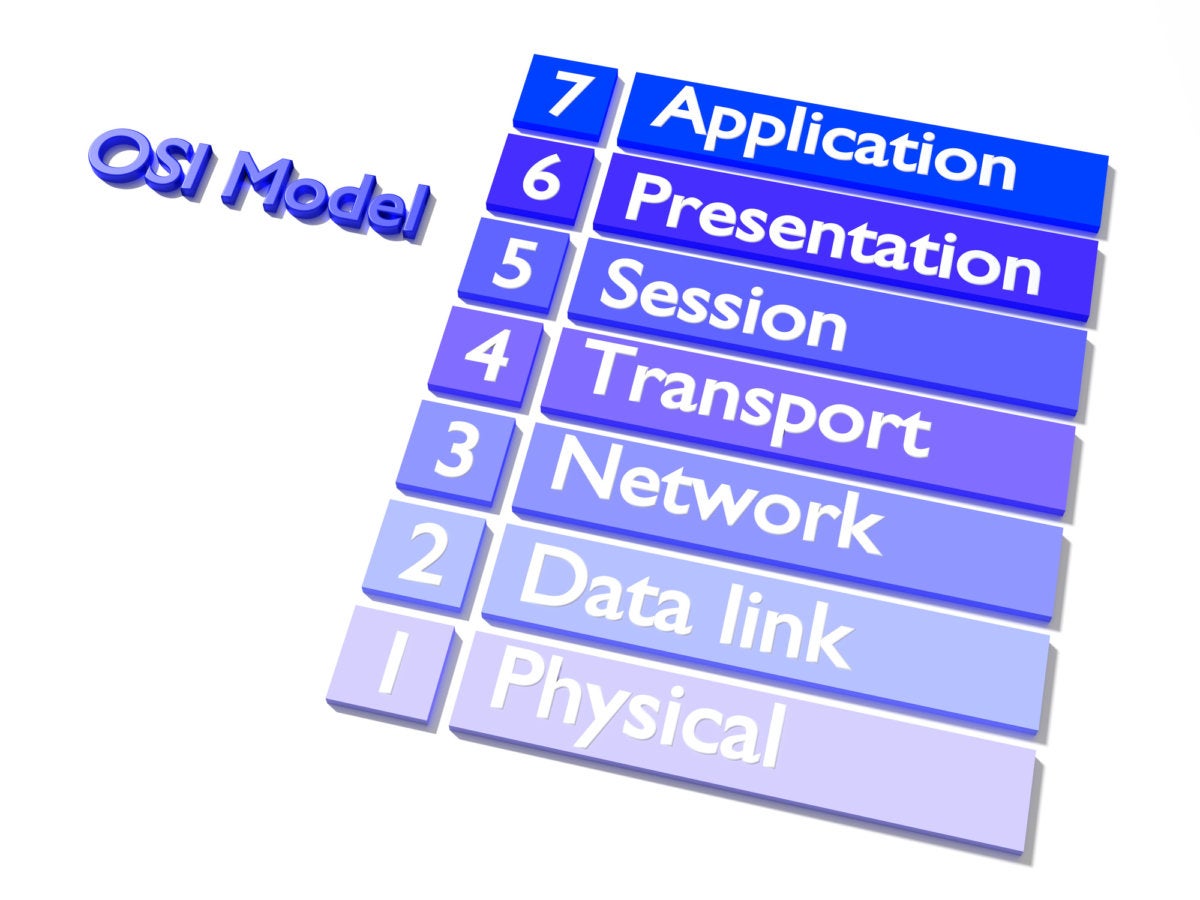
When most non-technical people hear the term “seven layers”, they either think of the popular Super Bowl bean dip or they mistakenly think about the seven layers of Hell, courtesy of Dante’s Inferno (there are nine). For IT professionals, the seven layers refer to the Open Systems Interconnection (OSI) model, a conceptual framework that describes the functions of a networking or telecommunication system. ... This can help network managers narrow down problems (Is it a physical issue or something with the application?), as well as computer programmers (when developing an application, which other layers does it need to work with?). Tech vendors selling new products will often refer to the OSI model to help customers understand which layer their products work with or whether it works “across the stack”.
What’s on the horizon for security and risk management leaders?

Security and risk management leaders are beginning to give more weight to the risks associated with the complex ecosystems that are an integral part of digital businesses: digital supply chain risk, third-party (and fourth- and fifth-party) risk, and so on. “Historically, it has been fairly straightforward to assess the financial risk of business relationships by leveraging business and credit rating services such as Standard and Poor’s, Dun and Bradstreet, and Moody’s. With regard to technical and cyber risk, there has been no standard framework or approach — or rather, there have been too many, with a minimal level of commonality or consistency,” the analysts pointed out. The demand is obviously there, but fulfilling it such a way that customers can be confident in the ratings is difficult. For one, the information based on which the ratings are calculated can’t be just from public sources.
Why Cybersecurity Must Be an International Effort
As countries strengthen their cyber capabilities, Painter explained, they need a stable environment so the beneficial parts of cyber aren't undermined by weak security. He said it's time for nations to discuss cyber policies through the United Nations and multi-government organizations instead of going solo. International law applies in cyberspace, he said; it isn't a "lawless space" where "anything goes." It sounds simple on the surface but is complex in practice. According to Painter, international agreements must focus on how to prevent cyberattacks that don't necessarily qualify as cyber warfare; right now, policies don't address these types of threats. States shouldn't attack the critical infrastructure of other states, for example. They shouldn't attack one another's computer emergency response teams (CERTs), something Painter likened to "going after ambulances on the battlefield."
Microsoft launches low-code platform to speed enterprise IoT development

Microsoft IoT Central is now in public preview, bringing IoT skills to more frontline workers with the help of low-code development, according to a Microsoft blog post. The scalable SaaS solution is built on Microsoft Azure and supports enterprise security, IoT best practices, and more. With the new solution, Microsoft handles the infrastructure, allowing end users to focus on creating IoT solutions that can value to their organization. According to the post, "Microsoft IoT Central makes it so that everyone can benefit from IoT." Microsoft's Azure IoT Hub will act as the cloud gateway for Microsoft IoT Central, the post said. This allows users to securely connect, provision, and update devices, as well as send them commands. It can support millions of connected devices, the release said.
Support for CDOs growing among businesses
This comes across in a new survey of 287 CDOs, chief analytics officers and other high-level data and analytics leaders from around the world. The 2017 study, conducted by technology researcher Gartner, revealed growing use of the Chief Data Officer title and an increase in the number of organizations that have instituted an Office of the CDO. Moreover, for the first time, more than half of CDOs now report directly to a member of the C-suite, another board member or the business owner. "The steady maturation of the office of the CDO underlines the acceptance and broader understanding of the role and recognizes the impact and value CDOs worldwide are providing," notes Michael Moran, a research director at Gartner. Budgets are also on the rise. Survey respondents report an average CDO office budget of $8 million—up 23 percent from the $6.5 million average reported in 2016.
Quote for the day:
"I not only use all the brains I have, but all I can borrow." -- Woodrow Wilson
No comments:
Post a Comment